Conti - THM
Conti, is a medium rated room. Use splunk to investigate the conti ransonmware

Conti, is a medium rated room. Use splunk to investigate the conti ransonmware
Can you identify the location of the ransomware?
Using the search query we find cmd.exe located in the documents folder. This is suspicious since cmd is usually in the system32 folder
sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" image: Image="C:\*.exe"
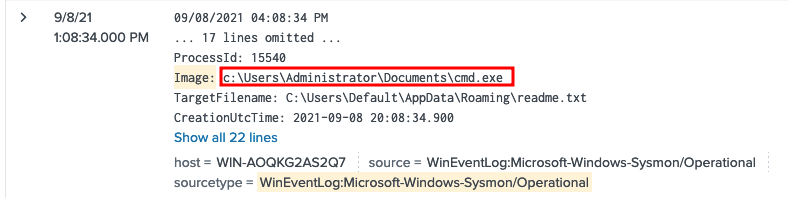
What is the Sysmon event ID for the related file creation event?
We browse the sysmon documentation and find event id 11 is for file create
Can you find the MD5 hash of the ransomware?
Now that we know which binary is malicious, we can filter for the hash
sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" "c:\\Users\\Administrator\\Documents\\cmd.exe"
| top Hashes
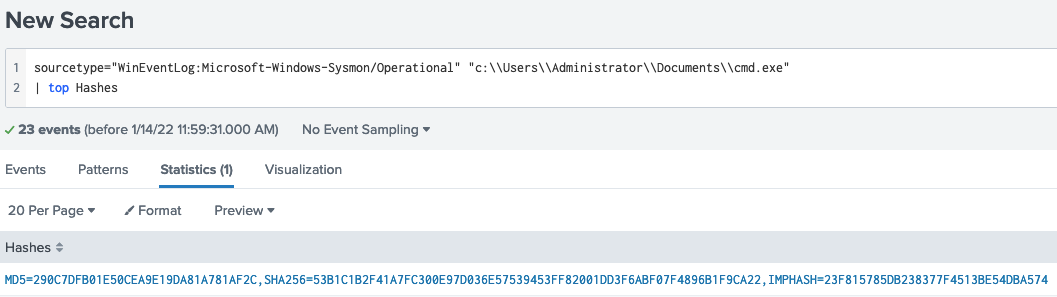
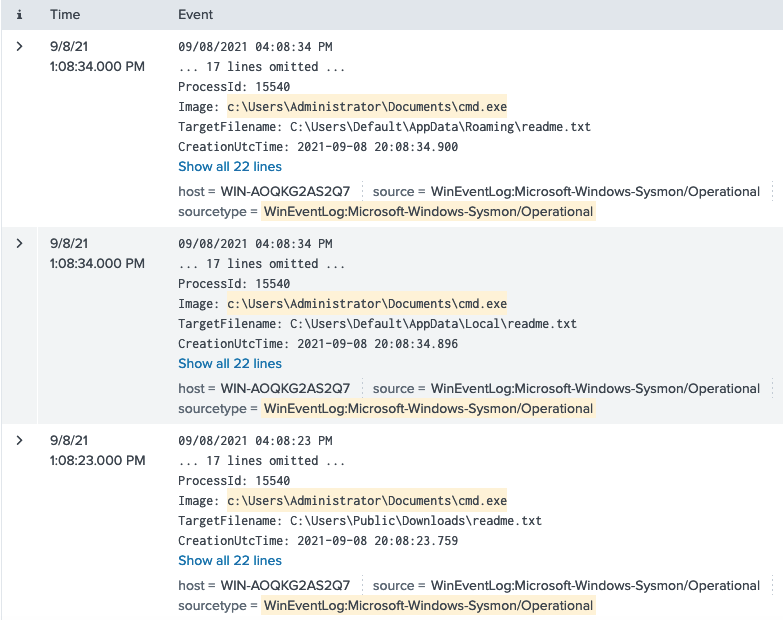
What file was saved to multiple folder locations?
Filtering for EventCode="11" we can find which files were created by this binary. We see readme.txt is saved in multiple locations.
sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" "c:\\Users\\Administrator\\Documents\\cmd.exe" EventCode="11"
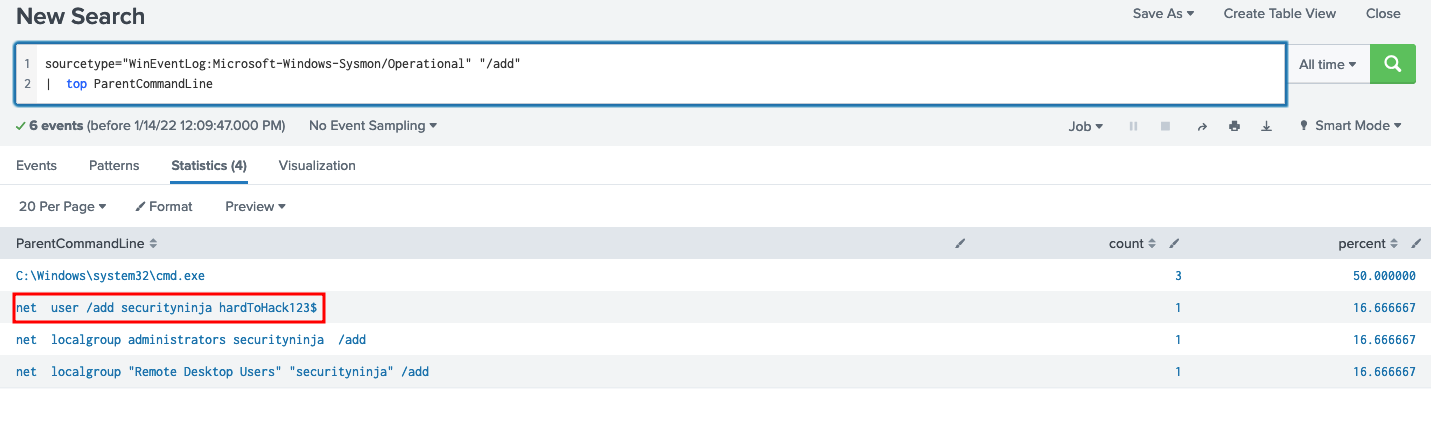
What was the command the attacker used to add a new user to the compromised system?
To find which user was added, we can search for /add to find which user was added
sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" "/add"
| top ParentCommandLine
The attacker migrated the process for better persistence. What is the migrated process image (executable), and what is the original process image (executable) when the attacker got on the system?
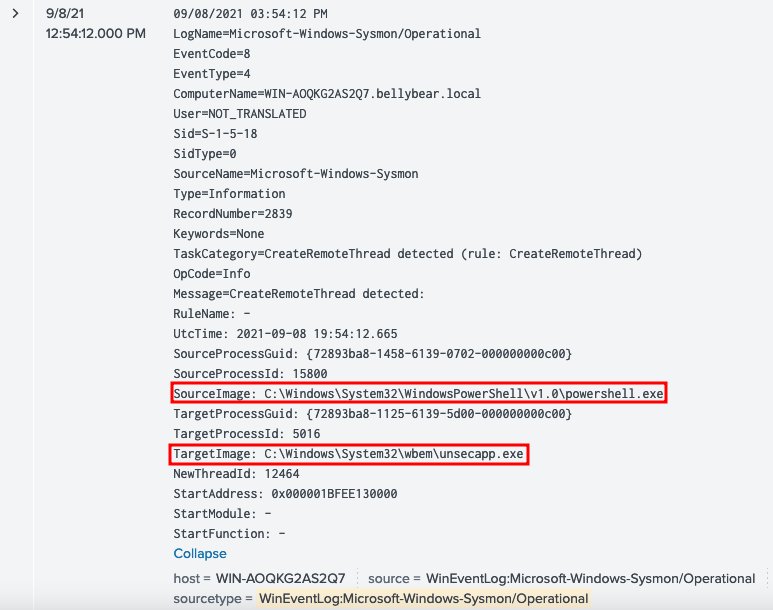
Searching for EventCode=8 we find which process was used to create a RemoteThread. There are two events, however we use the first event
sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" EventCode="8"
The attacker also retrieved the system hashes. What is the process image used for getting the system hashes?
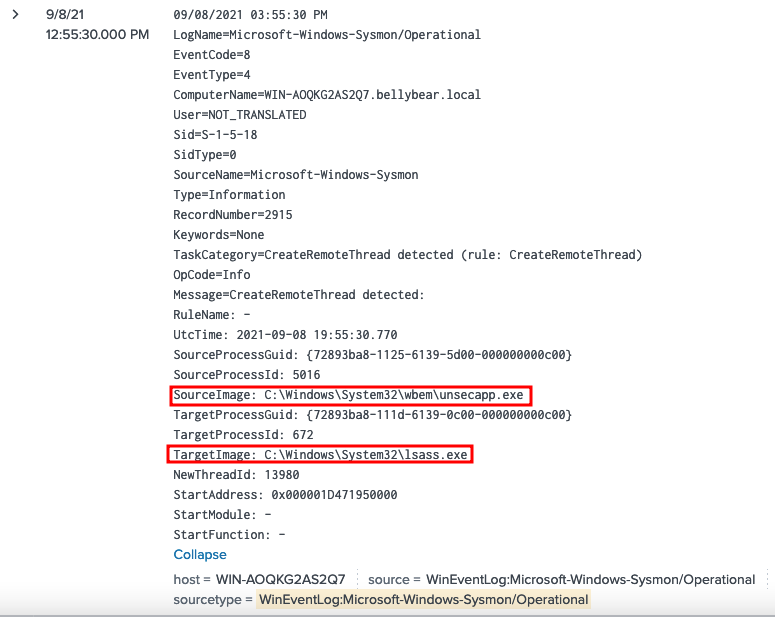
Using the second event from the previous answer, we see that the unsecapp.exe injected itself to lsass.exe. lsass.exe is responsible for authentication on windows domain
What is the web shell the exploit deployed to the system?
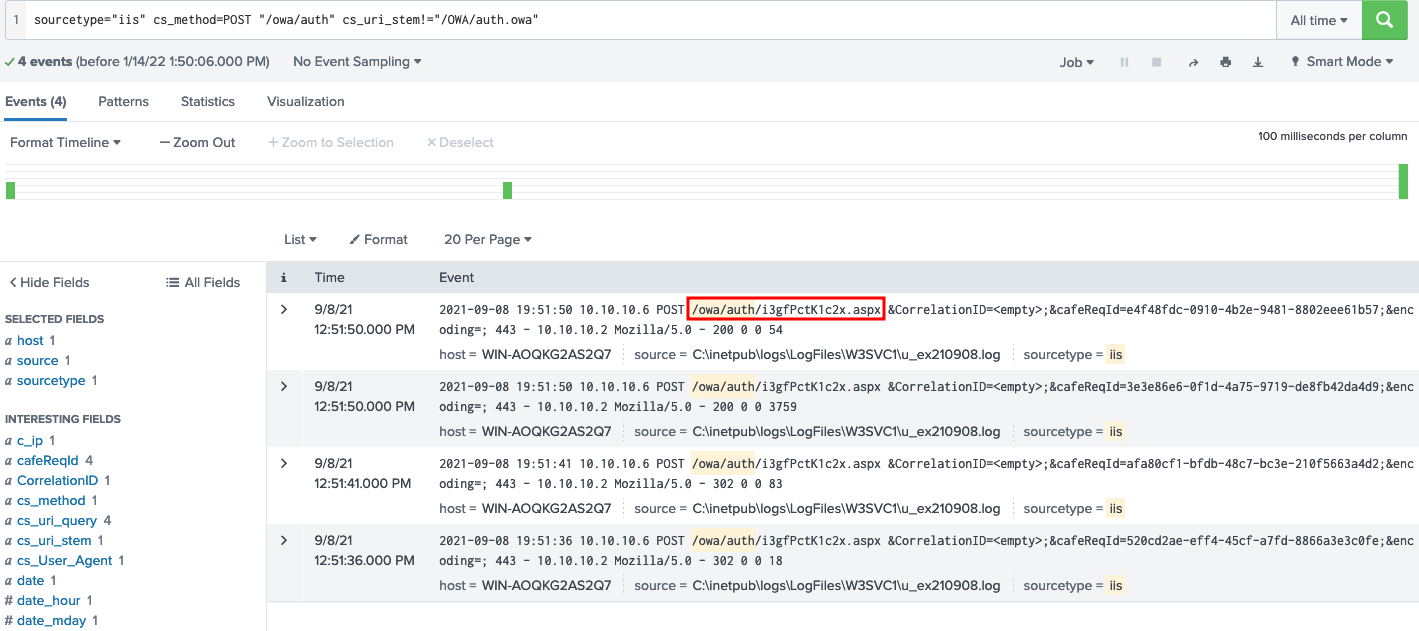
After getting nowhere, a quick search on how to detect webshell using splunk, lead me here. Some of the vulnerable paths are\HttpProxy\owa\auth\, \inetpub\wwwroot\aspnet_client\, and \HttpProxy\OAB\. We start searching splunk for these path and we find a suspicious aspx file
sourcetype="iis" cs_method=POST "/owa/auth" cs_uri_stem!="/OWA/auth.owa"
What is the command line that executed this web shell?
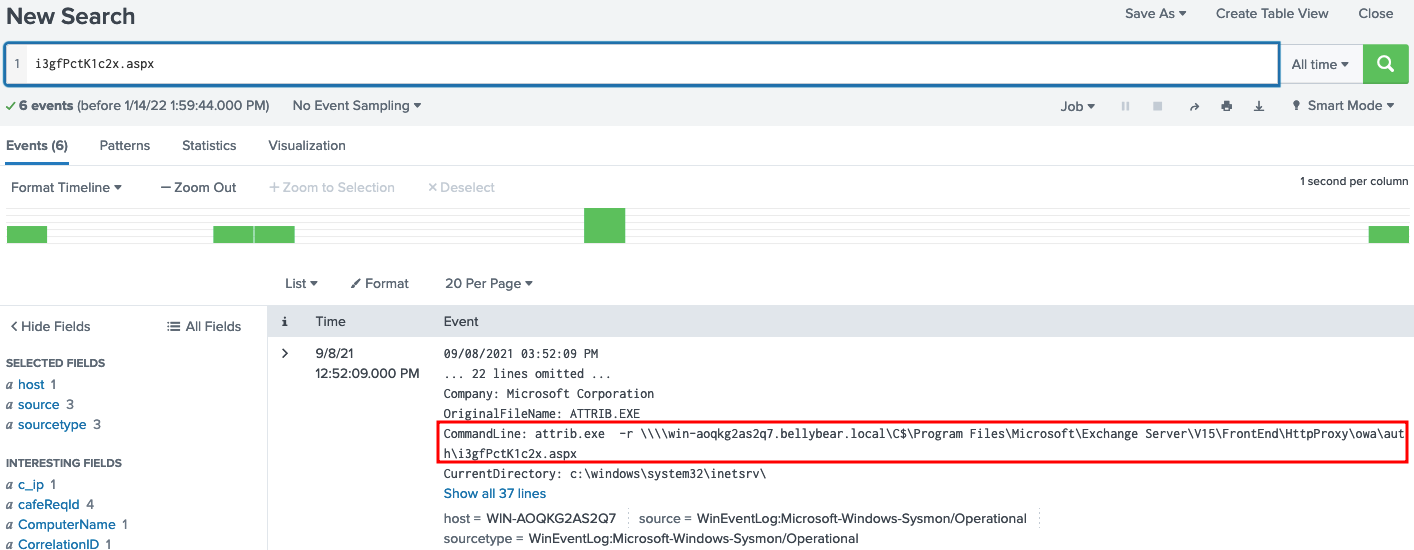
Now that we know the webshell name, we can search for i3gfPctK1c2x.aspx and the first hit shows us the command line used
What three CVEs did this exploit leverage?
The three CVE's this malware used are CVE-2020-0796,CVE-2018-13374, CVE-2018-13379
