Classic Passwd - THM
Classic Passwd, is a medium rated challenge. User obtained by using radare2

Classic Passwd, is a medium rated challenge. User obtained by using radare2
Reverse Engineering
For this challenge i used radare2 to reverse engineer the binary.
We start by load radare2 and run the challenge file in debug mode
r2 -d Challenge.Challenge
Afterwards we auto-analyze the binary to discover the strings and functions by running aaa
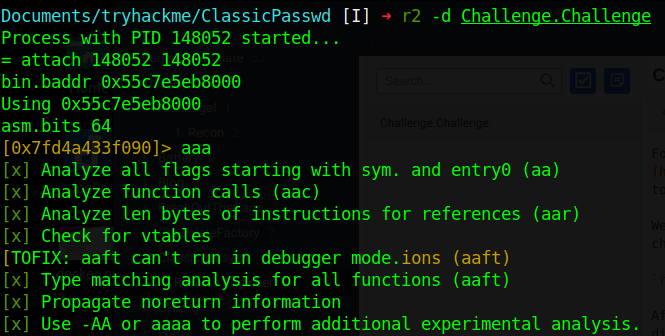
Now that we have analyzed the binary, we run afl to view the functions, which will list many functions. However we can start from the main function
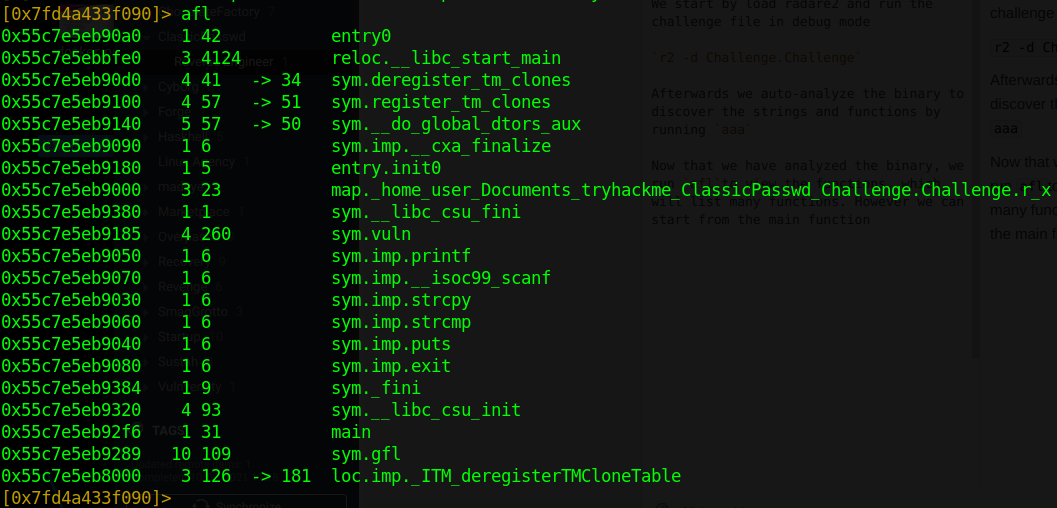
By running s main we can navigate to the main function henceforth print the dissassembly by running pdf
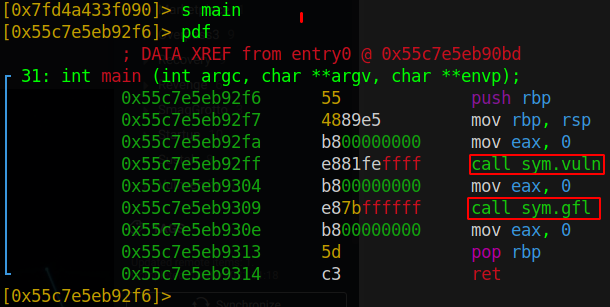
From the main function we see that it is calling two functions vuln and gfl
By repeating the previous step the can navigate to vuln and gfl, s sym.vuln and s sym.gfl, respectively. But the function we are interested in is sym.vuln to figure out the username to get the flag
Once we navigate to sym.vuln we can change our visual mode by pressing V and navigating the various GUI modes by pressing p. This allows us to view the registers and the stack
The instruction we are interested is at 0x55c7e5eb925a. This is where the string comparison is taking place, hence we can place a breakpoint at this address by scrolling, using the arrow keys, to the address and pressing f2 at which point you will see a b next to the address
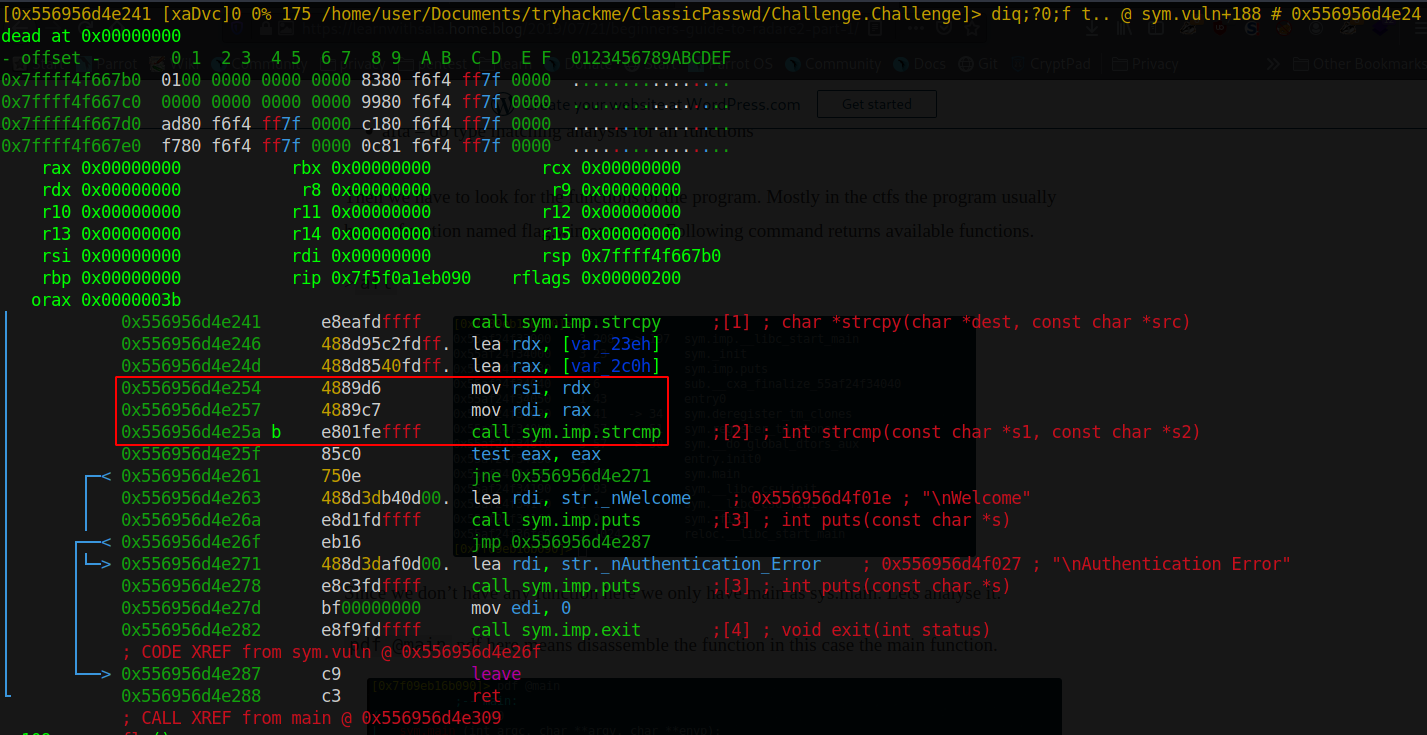
Once we have the breakpoint we can run the program until the breakpoint by pressing f9 at which point it will ask for our input. Once we input any name it will take us back to the breakpoint, as indicated by the rip instruction pointer
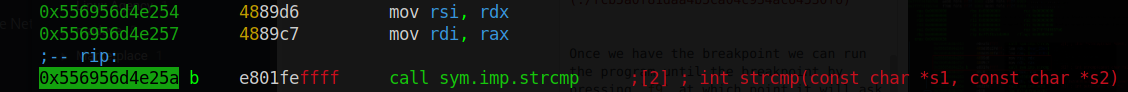
We do not have to continue execution at this point. To view the actual username we can print the rax and rdi registers. However to get to the command prompt by can press :
Once at the prompt we run pf z @ rax and pf z @ rdi. This simply means print a formatted string pf, at this address @ rdi which includes a null terminating string z.
The rdx register holds our username.
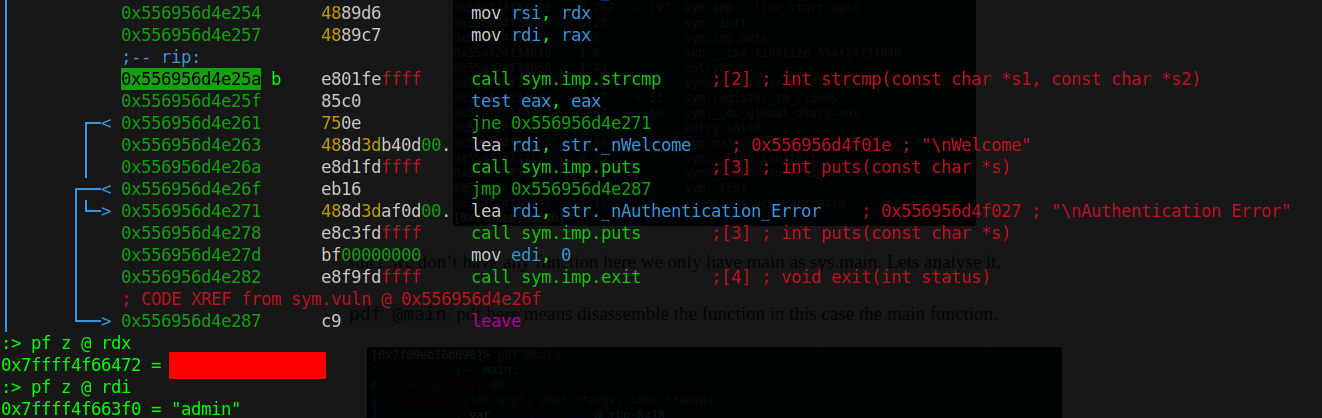
We now quit radare2 and run the binary with our new username and we get the flag.
Other Method
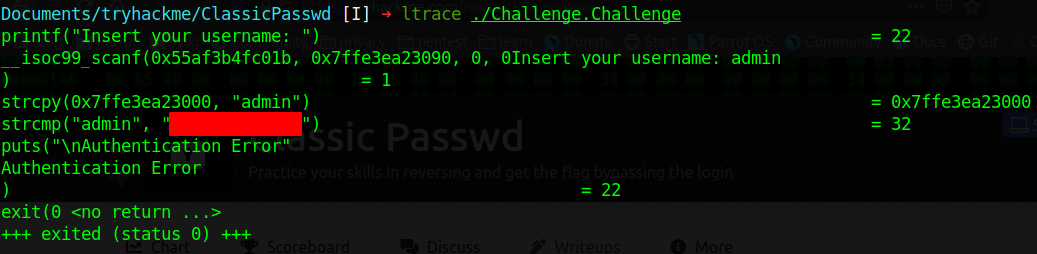
ltrace
After concluding the challenge and finishing my writeup I found another way to get the user by using ltrace
References:
